-
Notifications
You must be signed in to change notification settings - Fork 180
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Improving documentations for the AppControl Manager app (#487)
Added screenshots to each AppControl Manager document page. Added details about all of the new features implemented in AppControl Manager version 1.8.0.0 Removed some old docs belonging to the deprecated WDACConfig PowerShell module. Added new documents and articles related to App Control.
- Loading branch information
Showing
58 changed files
with
800 additions
and
3,281 deletions.
There are no files selected for viewing
File renamed without changes.
File renamed without changes.
26 changes: 26 additions & 0 deletions
26
...Business/Fast and Automatic Microsoft Recommended Driver Block Rules updates.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,26 @@ | ||
| # Fast and Automatic Microsoft Recommended Driver Block Rules updates | ||
|
|
||
| <br> | ||
|
|
||
| [The blocklist is updated with each new major release of Windows, typically 1-2 times per year](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules), but you can deploy the recommended driver block rules policy more frequently. | ||
|
|
||
| [This is the GitHub source](https://github.com/MicrosoftDocs/windows-itpro-docs/blob/public/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules.md) for the XML content shown on the Microsoft document website. You can see when the last time it was changed was, read the change history and commit messages. | ||
|
|
||
| Use the [**AppControl Manager**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) to **automate** the required [steps explained on the document](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules#steps-to-download-and-apply-the-vulnerable-driver-blocklist-binary) to download and deploy the recommended driver block rules. | ||
|
|
||
| <br> | ||
|
|
||
| 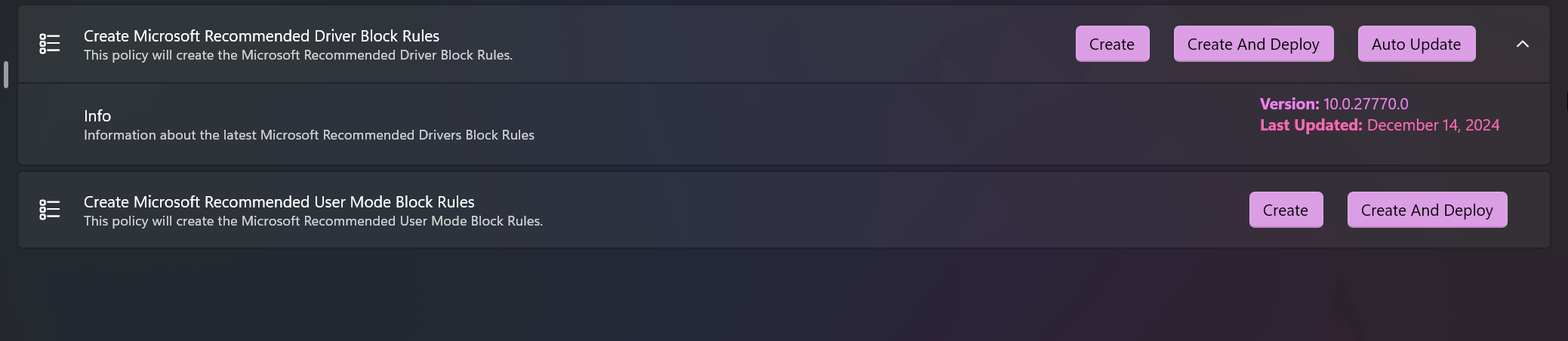 | ||
|
|
||
| <br> | ||
|
|
||
| The **Auto Update** button in [**the Create Policy page**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Create-App-Control-Policy) creates a scheduled task in Windows that will **automatically** run every 7 days to keep the block list up to date. | ||
|
|
||
| <br> | ||
|
|
||
| > [!NOTE]\ | ||
| > Microsoft recommended driver block rules that are enforced as a result of using either memory integrity (also known as hypervisor-protected code integrity or HVCI), Smart App Control, or S mode, are saved in a file called `driversipolicy.p7b` in the `%windir%\system32\CodeIntegrity` directory. | ||
| > | ||
| > The file you download from Microsoft document is called `SiPolicy.p7b` and it won't overwrite the `driversipolicy.p7b` once deployed. It will work side-by-side the default block rules and will be enforced as well. They are both explicit deny base policies. | ||
| <br> |
59 changes: 59 additions & 0 deletions
59
...ts/App Control for Business/How To Create an App Control Supplemental Policy.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,59 @@ | ||
| # How To Create an App Control Supplemental Policy | ||
|
|
||
| Base policies that have the `Enabled:Allow Supplemental Policies` [rule option](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-1-app-control-for-business-policy---policy-rule-options) can be extended with supplemental policies. Supplemental policies can be used to expand the scope of a base policy without modifying the base policy itself. This allows you to create a base policy that is shared across multiple devices and then create supplemental policies that are specific to individual devices or groups of devices. | ||
|
|
||
| You can have as many supplemental policies as you need, but each supplemental policy can only be associated with one base policy. | ||
|
|
||
| > [!TIP]\ | ||
| > How to differentiate between base and supplemental policies: | ||
| > | ||
| > The values of `PolicyID` and `BasePolicyID` fields in a base policy are the same, but in a supplemental policy, the `BasePolicyID` field contains the `PolicyID` of the base policy it is associated with. | ||
| > | ||
| > There are other signs that indicate if a policy is a base or supplemental policy. A supplemental policy can only contain allow rules. A supplemental policy can only have a subset of [the rule options](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-1-app-control-for-business-policy---policy-rule-options). | ||
| > | ||
| > Use the [System Information page](https://github.com/HotCakeX/Harden-Windows-Security/wiki/System-Information) in the [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) to view all of the deployed policies and see which ones are base or supplemental. | ||
| > | ||
| When it comes to signing, if the base policy is signed, then the supplemental policy must be signed too and vise versa. | ||
|
|
||
| <br> | ||
|
|
||
| ## Create a Supplemental Policy By Scanning Files and Folders | ||
|
|
||
| Assuming you've already deployed a base policy, you can create a supplemental policy by navigating to the [**Create Supplemental Policy Page**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Create-Supplemental-App-Control-Policy). | ||
|
|
||
| In the **Files and Folders section**, browse for your base policy's XML file. Enter a descriptive name for the supplemental policy that will be created and browse for files and/or folder to scan. If you select folders, they will be scanned recursively, meaning any file in the sub-folders will also be included in the scan. | ||
|
|
||
| The default [level](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-Rule-Levels-Comparison-and-Guide) is set to `File Publisher` but you can change it to another level that meets your needs. | ||
|
|
||
| <br> | ||
|
|
||
| <div align="center"> | ||
|
|
||
| <img src="https://raw.githubusercontent.com/HotCakeX/.github/8efca7547427750d599edd6f429be326c7010292/Pictures/PNG%20and%20JPG/How%20To%20Create%20an%20App%20Control%20Supplemental%20Policy/Files%20and%20Folders%20supplemental%20policy%20creation.png" alt="Create a Supplemental Policy By Scanning Files and Folders"> | ||
|
|
||
| </div> | ||
|
|
||
| <br> | ||
|
|
||
| <br> | ||
|
|
||
| After you've submitted the necessary details, press the `Create Supplemental Policy` button. The scan will begin and you will be able to view the progress in real time. If you toggle the `Deploy After Creation` button, the policy will be automatically deployed on the local system, otherwise the XML file will just be created. | ||
|
|
||
| You can customize the XML file further using different pages and features of the AppControl Manager. | ||
|
|
||
| <br> | ||
|
|
||
| ### FAQs | ||
|
|
||
| Q: What happens if you create a supplemental policy with the same name as an existing one? | ||
|
|
||
| A: Although not recommended as it will make it hard to differentiate between the two in [System Information](https://github.com/HotCakeX/Harden-Windows-Security/wiki/System-Information), you can create a supplemental policy with the same name as an existing one. It won't overwrite the existing one as they will still have different PolicyIDs. | ||
|
|
||
| <br> | ||
|
|
||
| Q: What if you create a supplemental policy for an app and then that app is updated? | ||
|
|
||
| A: It all depends on the level you selected for the supplemental policy. If you selected `File Publisher` or `Publisher`, then the policy will still apply to the updated app as long as it is signed by the same publisher. If you selected `Hash`, then the policy will no longer apply to the updated app as the binaries are changed. You will have to scan the new binaries and create a new supplemental policy for them and preferably remove the old one. | ||
|
|
||
| <br> |
144 changes: 144 additions & 0 deletions
144
...App Control for Business/How To Generate Audit Logs via App Control Policies.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,144 @@ | ||
| # How To Generate Audit Logs via App Control Policies | ||
|
|
||
| Audit Logs are generated when a Base policy is deployed with `Audit Mode` rule option. You can configure rule options in policies via [AppControl Manager's features](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Configure-Policy-Rule-Options). | ||
|
|
||
| You can view all of the available rule options in the following [Microsoft Learn page](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-1-app-control-for-business-policy---policy-rule-options). | ||
|
|
||
| During the Audit mode phase, no file is blocked, instead an audit log in the `Code Integrity/Operational` or `AppLocker` event logs are generated for each file that is executed on the system that would have been blocked if the policy was deployed in enforced mode. | ||
|
|
||
| If the file is a `MSI` installer file or script, then `AppLocker` event is generated for it, otherwise `Code Integrity` will log that file. | ||
|
|
||
| The logs can be collected by the AppControl Manager in order to create Supplemental policies. The logs can also be collected in bulk from thousands of systems by the Microsoft Defender for Endpoint Advanced Hunting and then fed to the AppControl Manager to create Supplemental policies. | ||
|
|
||
| <br> | ||
|
|
||
| ## Create and Deploy a Base Policy | ||
|
|
||
| First, we have to deploy a base policy. The type of base policy we deploy will determine the kinds of audit logs that will be generated. There are 2 recommended types of base policies you can choose from for this particular scenario. | ||
|
|
||
| 1. **Default Windows**, allows the following files and components: | ||
|
|
||
| * Windows Operating System Components | ||
|
|
||
| * Apps installed directly from the Microsoft Store | ||
|
|
||
| * Microsoft 365 apps | ||
|
|
||
| * WHQL-signed Drivers | ||
|
|
||
| 2. **Allow Microsoft**, allows the following files and components: | ||
|
|
||
| * Everything that Default Windows policy allows | ||
|
|
||
| * All files and programs signed by Microsoft's certificates. | ||
|
|
||
| <br> | ||
|
|
||
| <div align="center"> | ||
|
|
||
| <img src="https://raw.githubusercontent.com/HotCakeX/.github/refs/heads/main/Pictures/PNG%20and%20JPG/How%20To%20Generate%20Audit%20Logs%20via%20App%20Control%20Policies/Base%20policy%20deployment.png" alt="Base policy deployment in audit mode"> | ||
|
|
||
| </div> | ||
|
|
||
| <br> | ||
|
|
||
| <br> | ||
|
|
||
| Choose one of the base policies and press the `Create And Deploy` button. After few seconds the policy will be deployed on the system. | ||
|
|
||
| If you want to deploy it on remote systems via Intune, press the `Create` button instead and then use the XML file in the Intune portal for remote deployment. | ||
|
|
||
| <br> | ||
|
|
||
| <img src="https://github.com/HotCakeX/Harden-Windows-Security/raw/main/images/Gifs/1pxRainbowLine.gif" width= "300000" alt="horizontal super thin rainbow RGB line"> | ||
|
|
||
| <br> | ||
|
|
||
| ## Generate Audit Event Logs on the System | ||
|
|
||
| To generate audit event logs, start by installing or running the programs and files you want to create a Supplemental policy for. If a program or file is not permitted by the deployed policy in Audit mode, an audit log will be created for it. | ||
|
|
||
|
|
||
| ### Examples | ||
|
|
||
| * If the Default Windows policy is deployed and you install or run applications like GitHub Desktop or Visual Studio, audit logs will be generated since these programs are not permitted by the Default Windows policy. | ||
|
|
||
| * Similarly, deploying the Allow Microsoft policy and then installing a third-party application like VLC Media Player will trigger audit logs for every file executed within that program, as it is not permitted by the Allow Microsoft base policy. | ||
|
|
||
| Keep in mind that only files that are executed during audit mode phase generate event logs, so by simply installing a program using its installer, we can't trigger event log generation for each of the components and executables that each program has. So, after installing the programs, run them, use them a bit as you normally would so that all of the programs' components are executed and event logs generated for them. | ||
|
|
||
| <br> | ||
|
|
||
| <img src="https://github.com/HotCakeX/Harden-Windows-Security/raw/main/images/Gifs/1pxRainbowLine.gif" width= "300000" alt="horizontal super thin rainbow RGB line"> | ||
|
|
||
| <br> | ||
|
|
||
| ## Scan the Event Logs | ||
|
|
||
| Navigate to the [AppControl Manager's Event Logs page](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Create-Policy-From-Event-Logs), then press the `Scan Logs` Button. | ||
|
|
||
| <br> | ||
|
|
||
| <div align="center"> | ||
|
|
||
| <img src="https://raw.githubusercontent.com/HotCakeX/.github/refs/heads/main/Pictures/PNG%20and%20JPG/How%20To%20Generate%20Audit%20Logs%20via%20App%20Control%20Policies/Event%20Logs%20Scan%20Logs%20Button.png" alt="Scan Logs Button in AppControl Manager app"> | ||
|
|
||
| </div> | ||
|
|
||
| <br> | ||
|
|
||
| <br> | ||
|
|
||
| AppControl Manager will begin scanning all of the related logs in Code Integrity and AppLocker events. Blocked and Audits events will both be included. You can use various User Interface elements and features to filter the logs such as by sorting the columns, filtering based on the date and so on. | ||
|
|
||
| <br> | ||
|
|
||
| <div align="center"> | ||
|
|
||
| <img src="https://raw.githubusercontent.com/HotCakeX/.github/refs/heads/main/Pictures/PNG%20and%20JPG/How%20To%20Generate%20Audit%20Logs%20via%20App%20Control%20Policies/Date%20based%20filtering.png" alt="Date based filtering in AppControl Manager Event Logs scan"> | ||
|
|
||
| </div> | ||
|
|
||
| <br> | ||
|
|
||
| <br> | ||
|
|
||
| Once you're done with filtering the logs, press the `Create Policy` button's small arrow on the right. It will open a flyout with 3 options. The options are explained [in this page](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Create-Policy-From-Event-Logs#configuration-details). In this case, we need to select the middle option called `Base Policy File` and then select the `Browse` Button. A file picker dialog will open, allowing you to select the base policy XML file that you created and deployed earlier. | ||
|
|
||
| <br> | ||
|
|
||
| <div align="center"> | ||
|
|
||
| <img src="https://raw.githubusercontent.com/HotCakeX/.github/refs/heads/main/Pictures/PNG%20and%20JPG/How%20To%20Generate%20Audit%20Logs%20via%20App%20Control%20Policies/selecting%20base%20policy%20for%20audit%20logs%20supplemental.png" alt="Selecting Base policy XML file path in AppControl Manager"> | ||
|
|
||
| </div> | ||
|
|
||
| <br> | ||
|
|
||
| <br> | ||
|
|
||
| The `Create Policy` button's label is now changed to `Create Policy for Selected Base`. Press it and after few seconds it will create a Supplemental policy for all of the logs displayed in the page. | ||
|
|
||
| <br> | ||
|
|
||
| <div align="center"> | ||
|
|
||
| <img src="https://raw.githubusercontent.com/HotCakeX/.github/refs/heads/main/Pictures/PNG%20and%20JPG/How%20To%20Generate%20Audit%20Logs%20via%20App%20Control%20Policies/Create%20policy%20for%20the%20selected%20base.png" alt="Selecting Base policy XML file path in AppControl Manager"> | ||
|
|
||
| </div> | ||
|
|
||
| <br> | ||
|
|
||
| <br> | ||
|
|
||
| From the actions menu you can select to deploy the Supplemental policy after creation too, or you can modify the supplemental policy further using AppControl Manager's other pages. You can [Sign the policy](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-App-Control-Policy) and make it tamper-proof or [Merge](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Merge-App-Control-Policies) it with other policies. | ||
|
|
||
| <br> | ||
|
|
||
| ## Wrapping Up | ||
|
|
||
| By now, you should have a solid understanding of how to generate and work with audit logs using AppControl Manager. You've learned how to deploy base policies, trigger audit events, and scan logs to create supplemental policies. | ||
|
|
||
| So go ahead start experimenting, collect those logs, and build policies that fit your environment and if you’re ever unsure about the next steps, the [AppControl Manager documentation](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) is always there to help you out! Plus you can always ask any questions you might have [here on GitHub discussions](https://github.com/HotCakeX/Harden-Windows-Security/discussions). | ||
|
|
||
| <br> |
Oops, something went wrong.