]
-```
-
-## Description
-
-Use this parameter to create a new App Control **base policy** with different policy types and configurations.
-
-> [!NOTE]\
-> If the selected policy type is `DefaultWindows` and the detected PowerShell is not installed through Microsoft Store, the module will scan the PowerShell files and add them to the `DefaultWindows` base policy as allowed files so you will be able to continue using the module after deploying the policy.
-
-> [!Tip]\
-> The `SignedAndReputable` policy type uses ISG, [The Microsoft Intelligent Security Graph](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/use-appcontrol-with-intelligent-security-graph).
-
-## Parameters
-
-### -PolicyType
-
-There are 3 policy types you can choose from and they are listed below:
-
-
-
-| Type: |[String](https://learn.microsoft.com/en-us/dotnet/api/system.string)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Accepted values: | `AllowMicrosoft`, `DefaultWindows`, `SignedAndReputable` |
-| Default value: | None |
-| Required: | True |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -Deploy
-
-Indicates that the policy is to be deployed to the local machine.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -Audit
-
-Turns on Audit mode in the policy so that the policy will be auditing files after deployment instead of blocking them.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -TestMode
-
-Indicates that the created policy will have ***Enabled:Boot Audit on Failure*** and ***Enabled:Advanced Boot Options Menu*** [policy rule options](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-1-app-control-for-business-policy---policy-rule-options).
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -RequireEVSigners
-
-Indicates that the created policy will have [Require EV Signers](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/appcontrol-wizard-create-base-policy#advanced-policy-rules-description) policy rule option.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -EnableScriptEnforcement
-
-Enables [script enforcement](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/script-enforcement) in the created policy.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -LogSize
-
-> [!NOTE]\
-> This parameter is only available when the `-Audit` parameter is used.
-
-Specifies the log size for ***Microsoft-Windows-CodeIntegrity/Operational*** events. The values must be in the form of ``. e.g., 2MB, 10MB, 1GB, 1TB. The minimum accepted value is 1MB which is the default.
-
-
-
-| Type: |[UInt64](https://learn.microsoft.com/en-us/dotnet/api/system.uint64)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
- -
-
-
-
-
-## New-WDACConfig -GetUserModeBlockRules
-
-
-
-## Syntax
-
-```powershell
-New-WDACConfig
- [-GetUserModeBlockRules]
- [-Deploy]
-```
-
-## Description
-
-Downloads the latest [Microsoft Recommended User-Mode Block Rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/applications-that-can-bypass-appcontrol).
-
-## Parameters
-
-### -Deploy
-
-Indicates that the policy is to be deployed to the local machine.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
- -
-
-
-
-
-## New-WDACConfig -GetDriverBlockRules
-
-
-
-## Syntax
-
-```powershell
-New-WDACConfig
- [-GetDriverBlockRules]
- [-Deploy]
- [-AutoUpdate]
-```
-
-## Description
-
-Downloads the latest [Microsoft Recommended Drivers Block rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules).
-
-## Parameters
-
-### -Deploy
-
-Indicates that the policy is to be deployed to the local machine.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -AutoUpdate
-
-Creates a scheduled task that runs every 7 days to automatically perform [the official method](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules#steps-to-download-and-apply-the-vulnerable-driver-blocklist-binary) for updating Microsoft recommended driver block rules.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
\ No newline at end of file
diff --git a/Wiki posts/WDACConfig Module Main/Remove-CommonWDACConfig.md b/Wiki posts/WDACConfig Module Main/Remove-CommonWDACConfig.md
deleted file mode 100644
index d11b414c7..000000000
--- a/Wiki posts/WDACConfig Module Main/Remove-CommonWDACConfig.md
+++ /dev/null
@@ -1,148 +0,0 @@
-# Remove-CommonWDACConfig available parameters
-
-
-
-## Syntax
-
-```powershell
-Remove-CommonWDACConfig
- [-CertCN]
- [-CertPath]
- [-SignToolPath]
- [-UnsignedPolicyPath]
- [-SignedPolicyPath]
- [-StrictKernelPolicyGUID]
- [-StrictKernelNoFlightRootsPolicyGUID]
-```
-
-## Description
-
-Use this cmdlet to remove the values stored in the User Configurations JSON file. If you use it without any parameters it will delete the User configuration folder and everything in it, which is located in `C:\Users\UserName\.WDACConfig`
-
-## Parameters
-
-### -CertCN
-
-Removes the saved Certificate Common Name from User Configurations
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -CertPath
-
-Removes the saved Certificate path from User Configurations
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -SignToolPath
-
-Removes the saved SignTool.exe Path from User Configurations
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -UnsignedPolicyPath
-
-Removes the saved Unsigned Policy Path from User Configurations
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -SignedPolicyPath
-
-Removes the saved Signed Policy Path from User Configurations
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -StrictKernelPolicyGUID
-
-Removes the saved Strict Kernel Policy GUID from User Configurations
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -StrictKernelNoFlightRootsPolicyGUID
-
-Removes the saved Strict Kernel NoFlight Roots Policy GUID from User Configurations
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
diff --git a/Wiki posts/WDACConfig Module Main/Remove-WDACConfig.md b/Wiki posts/WDACConfig Module Main/Remove-WDACConfig.md
deleted file mode 100644
index e2c9a0f1f..000000000
--- a/Wiki posts/WDACConfig Module Main/Remove-WDACConfig.md
+++ /dev/null
@@ -1,173 +0,0 @@
-# Remove-WDACConfig available parameters
-
-## Remove-WDACConfig -SignedBase
-
-
-
-## Syntax
-
-```powershell
-Remove-WDACConfig
- [-SignedBase]
- -PolicyPaths
- [-CertCN ]
- [-SignToolPath ]
- [-Force]
- [-Confirm]
- []
-```
-
-## Description
-
-Uses [the official procedure](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/deployment/disable-appcontrol-policies) to Re-Deploy the Signed base App Control policies with ***Enabled:Unsigned System Integrity Policy*** rule option.
-
-## Parameters
-
-### -PolicyPaths
-
-Path to xml file(s) of the currently deployed policy that you want to remove. Supports tab completion by showing only `.xml` files.
-
-
-
-| Type: |[FileInfo](https://learn.microsoft.com/en-us/dotnet/api/system.io.fileinfo)[]|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | True |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -CertCN
-
-Common name of the certificate - Supports argument completion so you don't have to manually enter the Certificate's CN. Make sure the certificate is installed in the personal store of the user certificates, then press TAB to auto complete the name. You can however enter it manually if you want to.
-
-
-
-| Type: |[String](https://learn.microsoft.com/en-us/dotnet/api/system.string)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| [Automatic:](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig#about-automatic-parameters) | True |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -SignToolPath
-
-Press TAB to open the file picker GUI and browse for SignTool.exe
-
-> [!IMPORTANT]\
-> Refer [to this section](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig#the-logic-behind-the--signtoolpath-parameter-in-the-module) for more info
-
-
-
-| Type: |[FileInfo](https://learn.microsoft.com/en-us/dotnet/api/system.io.fileinfo)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| [Automatic:](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig#about-automatic-parameters) | True |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -Force
-
-Indicates that the cmdlet won't ask for confirmation and will proceed with redeploying the signed base policy in unsigned mode.
-
-
-
-| Type: |[SwitchParameter](https://learn.microsoft.com/en-us/dotnet/api/system.management.automation.switchparameter)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
- -
-
-
-
-
-## Remove-WDACConfig -UnsignedOrSupplemental
-
-
-
-## Syntax
-
-```powershell
-Remove-WDACConfig
- [-UnsignedOrSupplemental]
- [-PolicyNames ]
- [-PolicyIDs ]
- [-Force]
- [-Confirm]
- []
-```
-
-## Description
-
-Removes Unsigned deployed App Control policies as well as [Signed deployed Supplemental App Control policies](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-Notes#removing-supplemental-policies)
-
-> [!NOTE]\
-> When using `-PolicyNames` parameter, if multiple policies with the exact same name are deployed, when you press TAB, you will only see 1 of them, if you select it, all of the policies with that name will be removed. If that's not desired, consider using `-PolicyIDs` parameter instead.
-
-> [!NOTE]\
-> The auto-completion in these 2 parameters are smart. E.g., if there are 10 policies deployed on the system, you can press Tab to select 5 of them by IDs, but when you try to select the other 5 by their names, the name of the policies that you already selected by IDs don't show up anymore. This greatly reduces user error and simplifies the workflow for end user.
-
-## Parameters
-
-### -PolicyIDs
-
-The submitted values are verified against the currently deployed policies and if they match, the policies are removed.
-
-Just press TAB key and it will autofill the values for you based on the deployed policies. If you want to select multiple names, after each one, enter a comma `,` and then press TAB again to choose another name.
-
-
-
-| Type: |[String](https://learn.microsoft.com/en-us/dotnet/api/system.string)[]|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -PolicyNames
-
-The submitted values are verified against the currently deployed policies and if they match, the policies are removed.
-
-Just press TAB key and it will autofill the values for you based on the deployed policies. If you want to select multiple IDs, after each one, enter a comma `,` and then press TAB again to choose another ID.
-
-
-
-| Type: |[String](https://learn.microsoft.com/en-us/dotnet/api/system.string)[]|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
diff --git a/Wiki posts/WDACConfig Module Main/Set-CommonWDACConfig.md b/Wiki posts/WDACConfig Module Main/Set-CommonWDACConfig.md
deleted file mode 100644
index 5dcf67d96..000000000
--- a/Wiki posts/WDACConfig Module Main/Set-CommonWDACConfig.md
+++ /dev/null
@@ -1,152 +0,0 @@
-# Set-CommonWDACConfig available parameters
-
-
-
-## Syntax
-
-```powershell
-Set-CommonWDACConfig
- [[-CertCN] ]
- [[-CertPath] ]
- [[-SignToolPath] ]
- [[-UnsignedPolicyPath] ]
- [[-SignedPolicyPath] ]
- [[-StrictKernelPolicyGUID] ]
- [[-StrictKernelNoFlightRootsPolicyGUID] ]
- [[-LastUpdateCheck] ]
- [[-StrictKernelModePolicyTimeOfDeployment] ]
- [[-AutoUpdate] ]
- []
-```
-
-## Description
-
-Use this cmdlet to store the values for common and frequently used parameters so that you won't have to specify them again every time.
-
-All of the applicable cmdlets of the module automatically check the User Configuration file for any available input, if you don't specify values for their parameters. Learn more about the User Configuration file [here](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig#about-automatic-parameters).
-
-
-
-## An Example
-
-Instead of specifying all of the parameters for `Edit-SignedWDACConfig` cmdlet like this:
-
-```powershell
-Edit-SignedWDACConfig -AllowNewApps -SuppPolicyName "App 1" -CertPath "Path To Certificate.cer" -PolicyPaths "Path To Policy.xml" -CertCN "Certificate Common Name"
-```
-
-You can just run this
-
-```powershell
-Edit-SignedWDACConfig -AllowNewApps -SuppPolicyName "App 1"
-```
-
-If correct and valid values for the missing parameters exist in User Configuration file, the cmdlet will automatically detect and use them seamlessly.
-
-## Parameters
-
-### -CertCN
-
-Common Name of an installed certificate. Supports argument completion so you don't have to manually enter the Certificate's CN, just make sure the certificate is installed in the personal store of the user certificates, then press TAB to auto complete the name. You can however enter it manually if you want to.
-
-
-
-| Type: |[String](https://learn.microsoft.com/en-us/dotnet/api/system.string)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -CertPath
-
-Path to the certificate `.cer` file. Press TAB to open the file picker GUI and browse for a `.cer` file.
-
-
-
-| Type: |[FileInfo](https://learn.microsoft.com/en-us/dotnet/api/system.io.fileinfo)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -SignToolPath
-
-Press TAB to open the file picker GUI and browse for SignTool.exe
-
-
-
-| Type: |[FileInfo](https://learn.microsoft.com/en-us/dotnet/api/system.io.fileinfo)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -UnSignedPolicyPath
-
-Path to the xml file of an Unsigned policy. Supports file picker GUI.
-
-
-
-| Type: |[FileInfo](https://learn.microsoft.com/en-us/dotnet/api/system.io.fileinfo)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
-
-### -SignedPolicyPath
-
-Path to the xml file of a Signed policy. Supports file picker GUI.
-
-
-
-| Type: |[FileInfo](https://learn.microsoft.com/en-us/dotnet/api/system.io.fileinfo)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-### -AutoUpdate
-
-Enables/Disable check for and downloading of new version of the WDACConfig module whenever it's available.
-
-
-
-| Type: |[BooleanParameter](https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_booleans)|
-| :-------------: | :-------------: |
-| Position: | Named |
-| Default value: | None |
-| Required: | False |
-| Accept pipeline input: | False |
-| Accept wildcard characters: | False |
-
-
-
-
diff --git a/Wiki posts/WDACConfig Module Main/Test-CiPolicy.md b/Wiki posts/WDACConfig Module Main/Test-CiPolicy.md
index b59f37bf5..b9b97a3b1 100644
--- a/Wiki posts/WDACConfig Module Main/Test-CiPolicy.md
+++ b/Wiki posts/WDACConfig Module Main/Test-CiPolicy.md
@@ -1,7 +1,5 @@
# Test-CiPolicy available parameters
-
-
## Syntax
```powershell
diff --git a/Wiki posts/WDACConfig Module Main/WDACConfig.md b/Wiki posts/WDACConfig Module Main/WDACConfig.md
index cef5e412d..ffed1ccd6 100644
--- a/Wiki posts/WDACConfig Module Main/WDACConfig.md
+++ b/Wiki posts/WDACConfig Module Main/WDACConfig.md
@@ -3,64 +3,18 @@
> [!IMPORTANT]\
> This module is being deprecated. Use the new AppControl Manager application -> https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager
>
-> YouTube demo:
-> https://www.youtube.com/watch?v=SzMs13n7elE
-
-
-[**WDACConfig**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) is an advanced PowerShell module designed with the aim of automating [Application and File whitelisting in Windows](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/appcontrol) using App Control for Business. [You can always find its source code on GitHub](https://github.com/HotCakeX/Harden-Windows-Security/tree/main/WDACConfig) and Install it from [**PowerShell Gallery**](https://www.powershellgallery.com/packages/WDACConfig/).
-
-This page is also available [on my website.](https://spynetgirl.github.io/WDACConfig%20Module/WDACConfig/)
-
-
-
- -
-
-
-
-
-## Requirements
-
-* PowerShell Core latest version
-
- * Install from [GitHub](https://github.com/PowerShell/PowerShell/releases/latest) or [Microsoft Store](https://www.microsoft.com/store/productid/9MZ1SNWT0N5D)
-
-* Windows 11 latest version
-* Administrator Privileges
-* Internet Connection (for periodic update checks that happen every 30 minutes)
-
-
-
- -
-
-
-
+## Preview of the App
-## Features
+
-* Uses the [official documented methods of the ConfigCI module](https://learn.microsoft.com/en-us/powershell/module/configci/).
-
-* Checks for new version periodically and updates itself automatically when necessary.
-
- - [Controllable](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Set-CommonWDACConfig) using `Set-CommonWDACConfig -AutoUpdate $True/$False`.
-
-* Actively trying to design it with [Microsoft Security Development Lifecycle (SDL)](https://www.microsoft.com/en-us/securityengineering/sdl/) guidelines in mind.
-
-* The module goes through Extended Validation before each update is released to make sure everything works perfectly.
-
-* The module can be used for managing local systems, remote systems and Azure VMs.
-
-* Use `-Verbose` common parameter with each cmdlet of the WDACConfig module to see extra details and what's happening under the hood.
-
-
-
-

+
-## Install The Module
+
-```powershell
-Install-Module -Name 'WDACConfig' -Scope 'AllUsers' -Force
-```
+
@@ -68,106 +22,14 @@ Install-Module -Name 'WDACConfig' -Scope 'AllUsers' -Force
-## Video Guides
-
-| Video Link | Description |
-| :---: | :---: |
-|  | [Microsoft Defender For Endpoint Advanced Hunting With WDACConfig Module](https://youtu.be/oyz0jFzOOGA?si=tJbFbzRJNy79lUo7) |
-|
| [Microsoft Defender For Endpoint Advanced Hunting With WDACConfig Module](https://youtu.be/oyz0jFzOOGA?si=tJbFbzRJNy79lUo7) |
-|  | [Sandboxing-like capabilities in the App Control Policies](https://www.youtube.com/watch?v=cp7TaTNPZE0) |
-|
| [Sandboxing-like capabilities in the App Control Policies](https://www.youtube.com/watch?v=cp7TaTNPZE0) |
-|  | [Create, Deploy & Audit App Control Policies](https://www.youtube.com/watch?v=JSwrfe9zYY4) |
-|
| [Create, Deploy & Audit App Control Policies](https://www.youtube.com/watch?v=JSwrfe9zYY4) |
-|  | [How To Set And Query Secure Settings in App Control Policies](https://www.youtube.com/watch?v=hNpzYlOMCys) |
-|
| [How To Set And Query Secure Settings in App Control Policies](https://www.youtube.com/watch?v=hNpzYlOMCys) |
-|  | [How To Create And Deploy Signed App Control Policies](https://www.youtube.com/watch?v=nZ5c9ceaEwA) |
-|
| [How To Create And Deploy Signed App Control Policies](https://www.youtube.com/watch?v=nZ5c9ceaEwA) |
-| %20Policies%20Using%20The%20WDACConfig%20Module%20-%20low%20res.png) | [Simulating App Control Deployment in Windows](https://www.youtube.com/watch?v=A0bKDaeYomg) |
-|
| [Simulating App Control Deployment in Windows](https://www.youtube.com/watch?v=A0bKDaeYomg) |
-|  | [Create Code Signing Certificate Using Windows Server](https://youtu.be/RSYJ64BlS9Y?si=t6TlcYzsMwteG1M9) |
-
-
| [Create Code Signing Certificate Using Windows Server](https://youtu.be/RSYJ64BlS9Y?si=t6TlcYzsMwteG1M9) |
-
-
-
- -
-
-
-
-
-## WDACConfig Module's Table of Content
+## WDACConfig Module's Table of Content [Deprecated]
| Cmdlet Guide | Usage | PowerShell Console Help |
| :---: | :---: | :---: |
-| [New-WDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig) | Mainly for creating and deploying App Control policies | `Get-Help New-WDACConfig` |
| [New-SupplementalWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig) | To create and deploy Supplemental policies | `Get-Help New-SupplementalWDACConfig` |
-| [Remove-WDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Remove-WDACConfig) | To remove deployed App Control policies | `Get-Help Remove-WDACConfig` |
-| [Edit-WDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Edit-WDACConfig) | To edit deployed unsigned App Control policies | `Get-Help Edit-WDACConfig` |
| [Edit-SignedWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Edit-SignedWDACConfig) | To edit deployed signed App Control policies | `Get-Help Edit-SignedWDACConfig` |
-| [Deploy-SignedWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig) | To sign and deploy App Control policies | `Get-Help Deploy-SignedWDACConfig` |
-| [Confirm-WDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Confirm-WDACConfig) | To confirm deployment and check the status of App Control policies | `Get-Help Confirm-WDACConfig` |
| [New-DenyWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-DenyWDACConfig) | To create a deny mode App Control policy | `Get-Help New-DenyWDACConfig` |
-| [Set-CommonWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Set-CommonWDACConfig) | To add or edit user configurations for common WDACConfig parameters | `Get-Help Set-CommonWDACConfig` |
| [New-KernelModeWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New%E2%80%90KernelModeWDACConfig) | To create a Strict Kernel mode App Control policy for [total BYOVD protection](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-policy-for-BYOVD-Kernel-mode-only-protection) | `Get-Help New-KernelModeWDACConfig` |
-| [Get-CommonWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Get-CommonWDACConfig) | To display or fetch user configurations for common WDACConfig parameters | `Get-Help Get-CommonWDACConfig` |
-| [Invoke-WDACSimulation](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Invoke-WDACSimulation) | To simulate an App Control policy deployment quickly | `Get-Help Invoke-WDACSimulation` |
-| [Remove-CommonWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Remove-CommonWDACConfig) | To remove user configurations for common WDACConfig parameters | `Get-Help Remove-CommonWDACConfig` |
-| [Assert-WDACConfigIntegrity](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Assert-WDACConfigIntegrity) | To ascertain that the files in your local WDACConfig folder are identical to the ones in the cloud | `Get-Help Assert-WDACConfigIntegrity` |
-| [Build-WDACCertificate](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Build-WDACCertificate) | To create proper code signing certificates for App Control policy signing | `Get-Help Build-WDACCertificate` |
| [Test-CiPolicy](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Test-CiPolicy) | Tests a Code Integrity (App Control) Policy XML file against the Schema and shows the signers in a signed `.CIP` files | `Get-Help Test-CiPolicy` |
-| [Get-CiFileHashes](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Get-CiFileHashes) | Calculates the Authenticode hash and first page hash of the PEs with SHA1 and SHA256 algorithms | `Get-Help Get-CiFileHashes` |
-| [ConvertTo-WDACPolicy](https://github.com/HotCakeX/Harden-Windows-Security/wiki/ConvertTo-WDACPolicy) | Multi-Purpose & Powerful functionalities such as converting local and MDE logs to App Control Policies | `Get-Help ConvertTo-WDACPolicy` |
-| [Get-CIPolicySetting](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Get-CIPolicySetting) | Queries the Secure Settings among the deployed policies on the system | `Get-Help Get-CIPolicySetting` |
-
-
-
- -
-
-
-
-
-## User Configurations Directory
-
-The module stores user configurations and all of the outputs only in the following directory:
-
-```
-C:\Program Files\WDACConfig
-```
-
-It's an Admin-protected path that provides security against non-elevated users and processes.
-
-
-
-### The Temporary Files Are Stored in the Following Directory
-
-```
-C:\Program Files\WDACConfig\StagingArea
-```
-
-Each cmdlet of the module creates a subdirectory in the StagingArea to store its temporary files. The subdirectory is named after the cmdlet's name. At the end of the cmdlet's execution, the temporary subdirectory is deleted, unless the `-Debug` parameter is used.
-
-
-
- -
-
-
-
-
-## About Automatic Parameters
-
-A parameter with an **Automatic** value of True in the description means that the module will use its default value set by the [Set-CommonWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Set-CommonWDACConfig) cmdlet. This simplifies the process and avoids redundancy. However, if an Automatic parameter has no value in User Configurations and you do not specify one in the command line, you will encounter an error requesting a value. Specifying a value for an Automatic parameter in the command line supersedes its default value in User Configurations, so the module will disregard the value of that parameter in the User Configurations file.
-
-
-
-### The Logic Behind The -SignToolPath Parameter in the Module
-
-1. If [Windows SDK](https://developer.microsoft.com/en-us/windows/downloads/windows-sdk/) Signing Tools for Desktop Apps components is installed in the default location `C:\Program Files (x86)\Windows Kits`, then specifying `-SignToolPath` parameter isn't necessary as the SignTool.exe will be detected automatically.
-
-2. If Windows SDK Signing Tools for Desktop Apps components is not installed in the default location or you want to manually browse for the signtool.exe, then make sure you either specify its path using `Set-CommonWDACConfig -SignToolPath` or use the `-SignToolPath` parameter.
-
-3. If SignTool.exe path is available in user configurations then it will be automatically used.
-
-4. Specifying `-SignToolPath` parameter explicitly on the command line takes priority over auto detection and value in the user configurations.
-
-5. If SignTool.exe cannot be auto-detected and the user didn't specify it on the command line, you will receive a prompt to authorize the automatic download of the most recent SignTool.exe version from the official Microsoft servers. Upon confirmation, it will be saved in your user configurations and utilized by the cmdlet.
-
-
-
- -
-
-
-
-
-## Feedback and Feature Request
-
-If there are any feedback or feature requests regarding this module, please [open a new discussion/issue on GitHub.](https://github.com/HotCakeX/Harden-Windows-Security)
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/Fast and Automatic Microsoft Recommended Driver Block Rules updates.md b/Wiki posts/Windows Defender Application Control (WDAC)/Fast and Automatic Microsoft Recommended Driver Block Rules updates.md
deleted file mode 100644
index 6df251ded..000000000
--- a/Wiki posts/Windows Defender Application Control (WDAC)/Fast and Automatic Microsoft Recommended Driver Block Rules updates.md
+++ /dev/null
@@ -1,43 +0,0 @@
-# Fast and Automatic Microsoft Recommended Driver Block Rules updates
-
-
-
-[The blocklist is updated with each new major release of Windows, typically 1-2 times per year](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules), but you can deploy the recommended driver block rules policy more frequently.
-
-[This is the GitHub source](https://github.com/MicrosoftDocs/windows-itpro-docs/blob/public/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules.md) for the XML content shown on the Microsoft document website. You can see when the last time it was changed was, read the change history and commit messages. The script below **automates** the required [steps explained on the document](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules#steps-to-download-and-apply-the-vulnerable-driver-blocklist-binary) to download and deploy the recommended driver block rules. Make sure you are using the latest version of Windows.
-
-## Use the [WDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) Module
-
-
-
-You can use the [WDACConfig Module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig#new-wdacconfig--getdriverblockrules) to create a scheduled task in Windows that will **automatically** run the script below every 7 days.
-
-```powershell
-Install-Module -Name WDACConfig -Force
-New-WDACConfig -GetDriverBlockRules -AutoUpdate
-```
-
-
-The script
-
-```powershell
-try {
- Invoke-WebRequest -Uri 'https://aka.ms/VulnerableDriverBlockList' -OutFile VulnerableDriverBlockList.zip -ErrorAction Stop
-}
-catch {
- exit 1
-}
-Expand-Archive -Path .\VulnerableDriverBlockList.zip -DestinationPath 'VulnerableDriverBlockList' -Force
-Rename-Item -Path .\VulnerableDriverBlockList\SiPolicy_Enforced.p7b -NewName 'SiPolicy.p7b' -Force
-Copy-Item -Path .\VulnerableDriverBlockList\SiPolicy.p7b -Destination "$env:SystemDrive\Windows\System32\CodeIntegrity"
-citool --refresh -json
-Remove-Item -Path .\VulnerableDriverBlockList -Recurse -Force
-Remove-Item -Path .\VulnerableDriverBlockList.zip -Force
-exit 0
-```
-
-
-
-
-
-Microsoft recommended driver block rules that are enforced as a result of using either memory integrity (also known as hypervisor-protected code integrity or HVCI), Smart App Control, or S mode, are saved in a file called `driversipolicy.p7b` in the `%windir%\system32\CodeIntegrity` directory. The file you will be downloading from Microsoft document is called `SiPolicy.p7b` and it won't overwrite the `driversipolicy.p7b` but it will take precedence over the `driversipolicy.p7b` when deployed, because it has newer version and you can verify it after using CiTool by observing the Code Integrity event logs as described in the document.
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/Introduction.md b/Wiki posts/Windows Defender Application Control (WDAC)/Introduction.md
deleted file mode 100644
index 94d7b5912..000000000
--- a/Wiki posts/Windows Defender Application Control (WDAC)/Introduction.md
+++ /dev/null
@@ -1,85 +0,0 @@
-# What is Application Control for Business?
-
-
-

-
-
-Application control is crucial for protecting computer systems in today's threat landscape and offers a distinct advantage over traditional antivirus solutions. Specifically, application control uses tailored access, shifting from a model where all applications are assumed trustworthy to one where applications must earn trust before they can run.
-
-Devices where Application Control policies are deployed on can either be centrally managed via MDM, Intune etc. or they can be home devices, devices that are private and don't belong to any organization, the computer of someone that you want to keep very much safe and secure [so that even the device's owner can't willingly or forcefully compromise themselves,](https://github.com/HotCakeX/Harden-Windows-Security/wiki/How-to-Create-and-Deploy-a-Signed-WDAC-Policy-Windows-Defender-Application-Control) the possibilities are endless.
-
-
-
-> [!IMPORTANT]\
-> Use [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) for all of your Application Control and Code Integrity management needs. It is scalable, easy to use, enterprise-ready, Azure VM ready and more importantly, it is free, open-source and always will be that way.
-
-
-
-App Control puts the power of security directly in your hands, giving you complete control over your system and the systems you manage. Unlike other solutions that create dependency on other people, App Control eliminates the need to constantly chase and block new malware variants. Once you configure your system and define the apps and files that are permitted to run, everything else is automatically blocked.
-
-**It's time to shift from a reactive approach to a proactive one.**
-
-
-
-## Application Control Usage Levels
-
-There are many ways you can utilize Application Control features and here they are sorted by the level of restriction and protection they provide; From top (having the least restriction and protection) to bottom (having the most restriction and protection).
-
-1. Use Microsoft recommended driver block rules.
- - **No user action required**; The vulnerable driver blocklist is enabled by default for all devices using HVCI or Memory Integrity.
- - [The built-in driver blocklist is updated with each new major release of Windows, typically 1-2 times per year.](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules)
-
-2. Update Microsoft recommended driver block rules outside of the twice a year schedule.
- - The drivers block list itself [is updated more frequently](https://github.com/MicrosoftDocs/windows-itpro-docs/commits/public/windows/security/application-security/application-control/windows-defender-application-control/design/microsoft-recommended-driver-block-rules.md) than twice a year schedule, [use the AppControl Manager to setup a scheduled task that keeps the list up-to-date.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Fast-and-Automatic-Microsoft-Recommended-Driver-Block-Rules-updates)
-3. Use Microsoft recommended block rules + Recommended driver block rules
- - Use the [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) to easily deploy the User-Mode Microsoft recommended block rules on your system.
-4. Create WDAC policy for **Lightly managed devices**
- - [Microsoft's guide: Create a WDAC policy for lightly managed devices](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-policy-for-lightly-managed-devices)
- - [My guide: WDAC for Lightly Managed Devices](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-for-Lightly-Managed-Devices)
-5. Use [Smart App Control](https://support.microsoft.com/en-us/topic/what-is-smart-app-control-285ea03d-fa88-4d56-882e-6698afdb7003)
- - It's just a toggle in Windows Security under App & Browser control. It uses a special kind of WDAC policy that provides more protection than a lightly managed workstation but less protection than a fully managed workstation.
- - It uses both of Microsoft's recommended block rules.
-6. Use Smart App Control + [Strict Kernel-Mode WDAC Policy](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New%E2%80%90KernelModeWDACConfig)
-7. Create WDAC policy for **Fully managed devices**
- - The following scenarios provide the highest protection against any threats from any sources when cryptographically signed and deployed and properly configured.
- - [WDAC for Fully managed device - Variant 1](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-for-Fully-Managed-Devices)
- - [WDAC for Fully managed device - Variant 2](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-for-Fully-Managed-Devices--Variant-2)
- - [WDAC for Fully managed device - Variant 3](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-policy-for-Fully-managed-device---Variant-3)
- - [WDAC for Fully managed device - Variant 4](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-policy-for-Fully-managed-device---Variant-4)
- - [Microsoft's guide: Create a WDAC policy for fully managed devices](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-policy-for-fully-managed-devices)
- - [Microsoft's guide: Create a WDAC policy for fixed-workload devices (reference computer)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-policy-using-reference-computer)
- - [Microsoft's guide: Use audit events to create WDAC policy rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/deployment/audit-appcontrol-policies)
-
-
-
-## Plan for App Control for Business lifecycle policy management
-
-Microsoft provides the [following official document](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/plan-appcontrol-management) to understand the decisions you need to make to establish the processes for managing and maintaining Application Control policies. The rest of them are mentioned below at the **Resources** section.
-
-
-
-## Documents
-
-* [Application Control for Windows](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/appcontrol)
-* [Understand App Control for Business policy design decisions](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/understand-appcontrol-policy-design-decisions)
-* [Deploying App Control for Business policies](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/deployment/appcontrol-deployment-guide)
-* [Use multiple App Control for Business Policies](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/deploy-multiple-appcontrol-policies)
-* [Use audit events to create WDAC policy rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/deployment/audit-appcontrol-policies)
-* [Merge App Control for Business policies](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/deployment/merge-appcontrol-policies)
-* [Understand App Control for Business policy rules and file rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#app-control-for-business-policy-rules)
-* [Testing and Debugging AppId Tagging Policies](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/AppIdTagging/debugging-operational-guide-appid-tagging-policies)
-* [Editing existing base and supplemental WDAC policies with the Wizard](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/appcontrol-wizard-editing-policy)
-* [Creating a new Supplemental Policy with the Wizard](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/appcontrol-wizard-create-supplemental-policy)
-* [App Control for Business example base policies](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/example-appcontrol-base-policies)
-* [Configure the Application Identity service](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/applocker/configure-the-application-identity-service)
-* [Microsoft recommended driver block rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules)
-* [Microsoft recommended block rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/applications-that-can-bypass-appcontrol)
-* [Create a WDAC policy using a reference computer (for fixed-workload devices)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-policy-using-reference-computer)
-* [Create a WDAC policy for fully managed devices](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-policy-for-fully-managed-devices)
-* [Create a WDAC policy for lightly managed devices](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-policy-for-lightly-managed-devices)
-* [Guidance on Creating WDAC Deny Policies](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-deny-policy)
-* [Hypervisor-protected Code Integrity enablement](https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/oem-hvci-enablement)
-
-
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 1.md b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 1.md
deleted file mode 100644
index dd5b5326e..000000000
--- a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 1.md
+++ /dev/null
@@ -1,100 +0,0 @@
-# WDAC policy for Fully Managed device - Variant 1
-
-
-
-| Base policy type|Method used|Signed | Protection score 1-5 |
-| :-------------: | :-------------: | :-------------: | :-------------: |
-| Allow Microsoft / Default Windows | [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) | No | 4 |
-
-
-
-> [!NOTE]\
-> This variant helps you create and deploy an App Control policy for fully managed device ***using only Event Viewer audit logs.***
->
-> This scenario includes using explicit Allow rules for files and certificates/signers, anything not allowed by the policies we are going to make are automatically denied/blocked.
-
-
-
- -
-
-
-
-
-## Prepare a Virtual Machine
-
-Install Hyper-V role from optional Windows features if you haven't already.
-
-```powershell
-Enable-WindowsOptionalFeature -Online -FeatureName Containers-DisposableClientVM -All -norestart
-```
-
-
-
-Download the latest Windows `.ISO` file [from Microsoft website](https://www.microsoft.com/software-download/), create a new VM with it, install Windows and log in. Fully update Windows and then restart to apply the updates. You can create a Hyper-V checkpoint at this point so that you can return back to this clean state later on if you need to.
-
-
-
- -
-
-
-
-
-## Prepare a Base policy
-
-There are 2 types of base policies you can choose from.
-
-1. Allow Microsoft: Allows only files and apps that are signed by Microsoft's trusted root certificates.
-
-2. Default Windows: Allows only files and apps that come pre-installed by Windows.
-
-### Deploy the Allow Microsoft Audit Mode Base Policy
-
-```powershell
-New-WDACConfig -PolicyType AllowMicrosoft -Audit -LogSize 20MB
-```
-
-### Deploy the Default Windows Audit Mode Base Policy
-
-```powershell
-New-WDACConfig -PolicyType DefaultWindows -Audit -LogSize 20MB
-```
-
-* [Parameter Info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig)
-
-
-
-Depending on whichever of the option you choose, it deploys the base policy in audit mode. No reboot required.
-
-
-
- -
-
-
-
-
-## Generate Audit Event Logs on the System
-
-Install all of the programs that you want to allow in the App Control policy, on the VM. These are the programs that you want to allow to run and be installed on the target system once you've deployed the App Control policy.
-
-* Installing or running 3rd party non-Microsoft programs, while ***Allow Microsoft*** policy in Audit mode is deployed on the VM, generates event logs for each of the programs and their files.
-
-* Installing or running any program that doesn't come pre-installed by default with Windows, while **Default Windows** policy in Audit mode is deployed on the VM, generates event logs for each of the programs and their files.
-
-These event logs are exactly what we need to identify and create Allow rules for the detected files.
-
-Only files that are executed during audit mode phase generate event logs, so by simply installing a program using its installer, we can't trigger event log generation for each of the components and executables that each program has. So, after installing the programs, run them, use them a bit as you normally would so that all of the programs' components are executed and event logs generated for them.
-
-
-
- -
-
-
-
-
-## Generate Supplemental Policy From the Audit Event Logs
-
-Run the following command which will scan the local machine's Code Integrity and AppLocker logs and display them to you in a nice GUI (Graphical User Interface) window so that you can see detailed information of each file and choose which ones you want to include in the supplemental policy.
-
-```powershell
-ConvertTo-WDACPolicy -BasePolicyFile
-```
-
-The cmdlet offers a lot more features, [**you can read about them here**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/ConvertTo-WDACPolicy).
-
-
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 2.md b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 2.md
deleted file mode 100644
index 08905ead0..000000000
--- a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 2.md
+++ /dev/null
@@ -1,134 +0,0 @@
-# WDAC policy for Fully managed device - Variant 2
-
-
-
-| Base policy type|Method used|Signed | Protection score 1-5 |
-| :-------------: | :-------------: | :-------------: | :-------------: |
-| Default Windows | [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) | No | 4 |
-
-
-
-
-
-```mermaid
-flowchart TD
- A(Deploy Default Windows base policy) -->B(Identify Important apps that need Supplemental policy)
- B --> C[Create Supplemental policy based on App's directory]
- C --> D[Want to allow an entire directory?]
- D --> E[New-SupplementalWDACConfig -FilePathWildCards]
- C --> F[Want to Scan the app's install directory?]
- F --> G[New-SupplementalWDACConfig -Normal]
- B --> H[Is it a game Installed using Xbox app?]
- H --> I[Or Is it an app that installs drivers outside app's directory?]
- I --> J[Edit-WDACConfig -AllowNewApps]
-```
-
-> [!NOTE]\
-> *Every time I use the word "App", I'm referring to regular Win32 programs as well as Microsoft Store installed apps; Basically, any software that you can run.*
->
-> This scenario provides a very high protection level. Using the WDACConfig module, it's very easy to deploy, manage and maintain a system with this configuration.
-
-
-
- -
-
-
-
-
-## Deploy the Default Windows Base Policy on the System
-
-Start by deploying the Default Windows base policy on the system, which allows only files and apps that come pre-installed in Windows to run and anything else is blocked.
-
-Since this is an unsigned policy, no reboot is required but it's better to perform a reboot if you want the currently running non-Windows apps to stop running.
-
-
-
-```powershell
-New-WDACConfig -PolicyType DefaultWindows -Deploy
-```
-
-* [Cmdlet info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig)
-
-After deploying the base policy, you can create Supplemental policies to allow other apps that don't come by default with Windows to run. To do that, you have multiple options.
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for Apps Already Installed
-
-If you deployed the Default Windows base policy on a system that already had apps installed, you can create Supplemental policy for them using the following syntaxes:
-
-### Based on Signer Rules, Hashes, File Names Etc.
-
-```powershell
-New-SupplementalWDACConfig -Normal -ScanLocation "C:\Program Files\Program" -SuppPolicyName "App's Name" -PolicyPath "C:\DefaultWindowsPlusBlockRules.xml" -Deploy
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--normal)
-
-
-
-### Based on File Path With One or More Wildcard Characters
-
-```powershell
-New-SupplementalWDACConfig -FilePathWildCards -WildCardPath "C:\Program Files\Program\*" -SuppPolicyName "App's Name" -PolicyPath
-"C:\DefaultWindowsPlusBlockRules.xml" -Deploy
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--filepathwildcards)
-
-
-
-### Based on an Installed Windows App’s Name
-
-```powershell
-New-SupplementalWDACConfig -InstalledAppXPackages -PackageName "*App's name*" -SuppPolicyName "App's name" -PolicyPath "C:\DefaultWindowsPlusBlockRules.xml" -Deploy
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--installedappxpackages)
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for New App Installations or Apps Already Installed
-
-If the app you are trying to allow isn't installed and when you try to install it you see a blocked/error message, you can use the following syntaxes to allow them to run and then automatically create Supplemental policy for them.
-
-These methods also work for apps that were installed prior to deploying the Default Windows base policy and now you want to allow them to run by creating Supplemental policy for them.
-
-You can create a Supplemental policy for more than 1 app at a time by browsing for multiple apps' install directories using the commands below.
-
-### Based on App’s Install Directory and Other Signals
-
-```powershell
-Edit-WDACConfig -AllowNewApps -SuppPolicyName "App's Name" -PolicyPath "C:\DefaultWindowsPlusBlockRules.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Edit-WDACConfig#edit-wdacconfig--allownewapps)
-
-
-
- -
-
-
-
-
-## What to Do When There Is an Update for an Allowed App?
-
-If you've created a Supplemental policy for an app that is already installed and now there is a newer version of that app available, you have multiple options:
-
-1. If the Supplemental policy that you created to allow that app is based on FilePath with wildcards, then the app can be updated and no change in policy is required.
-
-2. If the Supplemental policy is based on [PFN (Package Family Name)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/manage-packaged-apps-with-appcontrol) of the app, available only for apps that use [MSIX](https://learn.microsoft.com/en-us/windows/msix/overview) installers, like some of the modern apps installed through Microsoft Store, then you don't need to take any action and the app will be updated without any issues.
-
-3. If the Supplemental policy is only based on the app's digital signature, which is common for well-made apps, then you don't need to take any further action. As long as the new version of the app has the same digital signature / developer identity, then it will be allowed to run.
-
-4. If the Supplemental policy is based on individual File Paths (in contrast to wildcard FilePath rules), or based on [FileName rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-3--specificfilenamelevel-options), then most likely there is no need for any further action to be taken as long as the new app's version uses the same file names or the same file paths for its components.
-
-5. If the Supplemental policy is based on Hash of the app's files, either partially (mixed with signer rules) or entirely (for apps without any digital identity/signature) then all you have to do is to remove the deployed Supplemental policy and create a new Supplemental policy for the app using live audit mode in the module as explained above. Don't need to reboot immediately, but to finish the removal process of a Supplemental policy, whether it's signed or unsigned, a reboot will be eventually needed.
-
-
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 3.md b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 3.md
deleted file mode 100644
index 4db4050fd..000000000
--- a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 3.md
+++ /dev/null
@@ -1,148 +0,0 @@
-# WDAC policy for Fully managed device - Variant 3
-
-
-
-| Base policy type|Method used|Signed | Protection score 1-5 |
-| :-------------: | :-------------: | :-------------: | :-------------: |
-| Allow Microsoft | [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) | Yes | 4.5 |
-
-
-
-
-
-```mermaid
-flowchart TD
- A(Deploy Allow Microsoft Signed base policy) -->B(Identify Important apps that need Supplemental policy)
- B --> C[Create Supplemental policy based on App's directory]
- C --> D[Want to allow an entire directory?]
- D --> E[New-SupplementalWDACConfig -FilePathWildCards]
- E --> AA[Deploy-SignedWDACConfig]
- C --> F[Want to Scan the app's install directory?]
- F --> G[New-SupplementalWDACConfig -Normal]
- G --> AB[Deploy-SignedWDACConfig]
- B --> H[Is it a game Installed using Xbox app?]
- H --> I[Or Is it an app that installs drivers outside app's directory?]
- I --> J[Edit-SignedWDACConfig -AllowNewApps]
-```
-
-> [!NOTE]\
-> *Every time I use the word "App", I'm referring to regular Win32 programs as well as Microsoft Store installed apps; Basically, any software that you can run.*
->
-> This scenario provides a very high protection level. Using the WDACConfig module, it's very easy to deploy, manage and maintain a system with this configuration.
-
-
-
- -
-
-
-
-
-## Deploy the Allow Microsoft Base Policy on the System
-
-Start by creating the Allow Microsoft base policy xml file, which allows only files and apps that are signed by Microsoft's trusted root certificate.
-
-```powershell
-New-WDACConfig -PolicyType AllowMicrosoft
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig)
-
-
-
-Now what we have the policy xml file for the Allow Microsoft base policy, we need to sign and deploy it.
-
-```powershell
-Deploy-SignedWDACConfig -CertPath "C:\Certificate.cer" -PolicyPaths "C:\AllowMicrosoftPlusBlockRules.xml" -CertCN "App Control Certificate" -Deploy
-```
-
-* [Cmdlet info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig)
-
-
-
-Since this is a signed base policy, you need to perform a reboot after deployment so that [the anti-tamper protection of a signed base policy](https://github.com/HotCakeX/Harden-Windows-Security/wiki/How-to-Create-and-Deploy-a-Signed-WDAC-Policy-Windows-Defender-Application-Control#if-someone-forcefully-deletes-the-deployed-wdac-policy-file) will start.
-
-After deploying the base policy, you can create Supplemental policies to allow other apps that aren't signed by Microsoft's trusted root certificate to run. To do that, you have multiple options.
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for Apps Already Installed
-
-If you deployed the Allow Microsoft base policy on a system that already had apps installed, you can create Supplemental policy for them using the following syntaxes. **After creating each Supplemental policy, you need to sign and deploy it [using the same Cmdlet we used above.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig)**
-
-### Based on Signer Rules, Hashes, File Names Etc.
-
-```powershell
-New-SupplementalWDACConfig -Normal -ScanLocation "C:\Program Files\Program" -SuppPolicyName "App's Name" -PolicyPath "C:\AllowMicrosoftPlusBlockRules.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--normal)
-
-
-
-### Based on File Path With One or More Wildcard Characters
-
-```powershell
-New-SupplementalWDACConfig -FilePathWildCards -WildCardPath "C:\Program Files\Program\*" -SuppPolicyName "App's Name" -PolicyPath
-"C:\AllowMicrosoftPlusBlockRules.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--filepathwildcards)
-
-
-
-### Based on an Installed Windows App’s Name
-
-```powershell
-New-SupplementalWDACConfig -InstalledAppXPackages -PackageName "*App's name*" -SuppPolicyName "App's name" -PolicyPath "C:\AllowMicrosoftPlusBlockRules.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--installedappxpackages)
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for New App Installations or Apps Already Installed
-
-If the app you are trying to allow isn't installed and when you try to install it you see a blocked/error message, you can use the following syntaxes to allow them to run and then automatically create Supplemental policy for them.
-
-These methods also work for apps that were installed prior to deploying the Allow Microsoft base policy and now you want to allow them to run by creating Supplemental policy for them.
-
-You can create a Supplemental policy for more than 1 app at a time by browsing for multiple apps' install directories using the commands below.
-
-
-
-### Based on App’s Install Directory and Other Signals
-
-```powershell
-Edit-SignedWDACConfig -AllowNewApps -CertPath "C:\Certificate.cer" -SuppPolicyName "App's Name" -PolicyPath "C:\AllowMicrosoftPlusBlockRules.xml" -CertCN "App Control Certificate"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Edit-SignedWDACConfig#edit-signedwdacconfig--allownewapps)
-
-
-
- -
-
-
-
-
-## What to Do When There Is an Update for an Allowed App?
-
-If you've created a Supplemental policy for an app that is already installed and now there is a newer version of that app available, you have multiple options:
-
-1. If the Supplemental policy that you created to allow that app is based on FilePath with wildcards, then the app can be updated and no change in policy is required.
-
-2. If the Supplemental policy is based on [PFN (Package Family Name)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/manage-packaged-apps-with-appcontrol) of the app, available only for apps that use [MSIX](https://learn.microsoft.com/en-us/windows/msix/overview) installers, like some of the modern apps installed through Microsoft Store, then you don't need to take any action and the app will be updated without any issues.
-
-3. If the Supplemental policy is only based on the app's digital signature, which is common for well-made apps, then you don't need to take any further action. As long as the new version of the app has the same digital signature / developer identity, then it will be allowed to run.
-
-4. If the Supplemental policy is based on individual File Paths (in contrast to wildcard FilePath rules), or based on [FileName rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-3--specificfilenamelevel-options), then most likely there is no need for any further action to be taken as long as the new app's version uses the same file names or the same file paths for its components.
-
-5. If the Supplemental policy is based on Hash of the app's files, either partially (mixed with signer rules) or entirely (for apps without any digital identity/signature) then all you have to do is to remove the deployed Supplemental policy and create a new Supplemental policy for the app using live audit mode in the module as explained above. Don't need to reboot immediately, but to finish the removal process of a Supplemental policy, whether it's signed or unsigned, a reboot will be eventually needed.
-
-
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 4.md b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 4.md
deleted file mode 100644
index 89b1ac014..000000000
--- a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Fully managed device - Variant 4.md
+++ /dev/null
@@ -1,146 +0,0 @@
-# WDAC policy for Fully managed device - Variant 4
-
-
-
-| Base policy type|Method used|Signed | Protection score 1-5 |
-| :-------------: | :-------------: | :-------------: | :-------------: |
-| Default Windows | [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) | Yes | 5 |
-
-
-
-
-
-```mermaid
-flowchart TD
- A(Deploy Default Windows Signed base policy) -->B(Identify Important apps that need Supplemental policy)
- B --> C[Create Supplemental policy based on App's directory]
- C --> D[Want to allow an entire directory?]
- D --> E[New-SupplementalWDACConfig -FilePathWildCards]
- E --> AA[Deploy-SignedWDACConfig]
- C --> F[Want to Scan the app's install directory?]
- F --> G[New-SupplementalWDACConfig -Normal]
- G --> AB[Deploy-SignedWDACConfig]
- B --> H[Is it a game Installed using Xbox app?]
- H --> I[Or Is it an app that installs drivers outside app's directory?]
- I --> J[Edit-SignedWDACConfig -AllowNewApps]
-```
-
-> [!NOTE]\
-> *Every time I use the word "App", I'm referring to regular Win32 programs as well as Microsoft Store installed apps; Basically, any software that you can run.*
->
-> This scenario provides the ultimate protection level. Using the WDACConfig module, it's very easy to deploy, manage and maintain a system with this configuration.
-
-
-
- -
-
-
-
-
-## Deploy the Default Windows Base Policy on the System
-
-Start by creating the Default Windows base policy xml file, which allows only files and apps that come pre-installed in Windows to run and anything else is blocked.
-
-```powershell
-New-WDACConfig -PolicyType DefaultWindows
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig)
-
-
-
-Now what we have the policy xml file for the Default Windows base policy, we need to sign and deploy it.
-
-```powershell
-Deploy-SignedWDACConfig -CertPath "C:\Certificate.cer" -PolicyPaths "C:\DefaultWindowsPlusBlockRules.xml" -CertCN "App Control Certificate" -Deploy
-```
-
-* [Cmdlet info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig)
-
-
-
-Since this is a signed base policy, you need to perform a reboot after deployment so that [the anti-tamper protection of a signed base policy](https://github.com/HotCakeX/Harden-Windows-Security/wiki/How-to-Create-and-Deploy-a-Signed-WDAC-Policy-Windows-Defender-Application-Control#if-someone-forcefully-deletes-the-deployed-wdac-policy-file) will start.
-
-After deploying the base policy, you can create Supplemental policies to allow other apps that don't come by default with Windows to run. To do that, you have multiple options.
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for Apps Already Installed
-
-If you deployed the Default Windows base policy on a system that already had apps installed, you can create Supplemental policy for them using the following syntaxes. **After creating each Supplemental policy, you need to sign and deploy it [using the same Cmdlet we used above.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig)**
-
-### Based on Signer Rules, Hashes, File Names Etc.
-
-```powershell
-New-SupplementalWDACConfig -Normal -ScanLocation "C:\Program Files\Program" -SuppPolicyName "App's Name" -PolicyPath "C:\DefaultWindowsPlusBlockRules.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--normal)
-
-
-
-### Based on File Path With One or More Wildcard Characters
-
-```powershell
-New-SupplementalWDACConfig -FilePathWildCards -WildCardPath "C:\Program Files\Program\*" -SuppPolicyName "App's Name" -PolicyPath
-"C:\DefaultWindowsPlusBlockRules.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--filepathwildcards)
-
-
-
-### Based on an Installed Windows App’s Name
-
-```powershell
-New-SupplementalWDACConfig -InstalledAppXPackages -PackageName "*App's name*" -SuppPolicyName "App's name" -PolicyPath "C:\DefaultWindowsPlusBlockRules.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--installedappxpackages)
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for New App Installations or Apps Already Installed
-
-If the app you are trying to allow isn't installed and when you try to install it you see a blocked/error message, you can use the following syntaxes to allow them to run and then automatically create Supplemental policy for them.
-
-These methods also work for apps that were installed prior to deploying the Default Windows base policy and now you want to allow them to run by creating Supplemental policy for them.
-
-You can create a Supplemental policy for more than 1 app at a time by browsing for multiple apps' install directories using the commands below.
-
-### Based on App's install directory and Other Signals
-
-```powershell
-Edit-SignedWDACConfig -AllowNewApps -CertPath "C:\Certificate.cer" -SuppPolicyName "App's Name" -PolicyPath "C:\DefaultWindowsPlusBlockRules.xml" -CertCN "App Control Certificate"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Edit-SignedWDACConfig#edit-signedwdacconfig--allownewapps)
-
-
-
- -
-
-
-
-
-## What to Do When There Is an Update for an Allowed App?
-
-If you've created a Supplemental policy for an app that is already installed and now there is a newer version of that app available, you have multiple options:
-
-1. If the Supplemental policy that you created to allow that app is based on FilePath with wildcards, then the app can be updated and no change in policy is required.
-
-2. If the Supplemental policy is based on [PFN (Package Family Name)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/manage-packaged-apps-with-appcontrol) of the app, available only for apps that use [MSIX](https://learn.microsoft.com/en-us/windows/msix/overview) installers, like some of the modern apps installed through Microsoft Store, then you don't need to take any action and the app will be updated without any issues.
-
-3. If the Supplemental policy is only based on the app's digital signature, which is common for well-made apps, then you don't need to take any further action. As long as the new version of the app has the same digital signature / developer identity, then it will be allowed to run.
-
-4. If the Supplemental policy is based on individual File Paths (in contrast to wildcard FilePath rules), or based on [FileName rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-3--specificfilenamelevel-options), then most likely there is no need for any further action to be taken as long as the new app's version uses the same file names or the same file paths for its components.
-
-5. If the Supplemental policy is based on Hash of the app's files, either partially (mixed with signer rules) or entirely (for apps without any digital identity/signature) then all you have to do is to remove the deployed Supplemental policy and create a new Supplemental policy for the app using live audit mode in the module as explained above. Don't need to reboot immediately, but to finish the removal process of a Supplemental policy, whether it's signed or unsigned, a reboot will be eventually needed.
-
-
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Lightly Managed Devices.md b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Lightly Managed Devices.md
deleted file mode 100644
index 2a5067df5..000000000
--- a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC for Lightly Managed Devices.md
+++ /dev/null
@@ -1,187 +0,0 @@
-# WDAC policy for Lightly managed device
-
-
-
-| Base policy type|Method used|Signed | Protection score 1-5 |
-| :-------------: | :-------------: | :-------------: | :-------------: |
-| [SignedAndReputable (ISG)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/use-appcontrol-with-intelligent-security-graph#configuring-isg-authorization-for-your-wdac-policy) | [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) | No / Yes | 3.5 / 4 |
-
-
-
-
-
-```mermaid
-flowchart TD
- A(Deploy App Control base policy with ISG) -->B(Start using your apps)
- B --> C(Did your app run without problem?)
- C -->|Yes| D[Awesome]
- C -->|No| E[Create a Supplemental policy for it]
-```
-
-> [!NOTE]\
-> *Every time I use the word "App", I'm referring to regular Win32 programs as well as Microsoft Store installed apps; Basically any software that you can run.*
->
-> This scenario provides a high protection level, ***higher if you cryptographically Sign it***. Using the WDACConfig module, it's very easy to deploy, manage and maintain a system with this configuration.
-
-
-
- -
-
-
-
-
-## Deploy the SignedAndReputable Base Policy on the System
-
-Start by deploying the SignedAndReputable base policy on the system, which allows only files and apps that are authorized by the [Intelligent Security Graph Authorization](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/use-appcontrol-with-intelligent-security-graph) which have known good state to run and anything else is blocked.
-
-### Unsigned version
-
-```powershell
-New-WDACConfig -PolicyType SignedAndReputable -Deploy
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig)
-
-
-
-### Signed version
-
-```powershell
-New-WDACConfig -PolicyType SignedAndReputable
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig)
-
-```powershell
-Deploy-SignedWDACConfig -CertPath "C:\Certificate.cer" -PolicyPaths "C:\Users\HotCakeX\SignedAndReputable.xml" -CertCN "App Control Certificate" -Deploy
-```
-
-* [Cmdlet info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig)
-
-
-
-* The module creates ***SignedAndReputable App Control base Policy*** based on [AllowMicrosoft policy template](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/example-appcontrol-base-policies) with ***ISG*** related [rule options](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-1-app-control-for-business-policy---policy-rule-options).
-
-* The module also automatically starts the [Application Identity](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/applocker/configure-the-application-identity-service) (`AppIDSvc`) service required for [ISG Authorization](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/use-appcontrol-with-intelligent-security-graph#enable-the-necessary-services-to-allow-wdac-to-use-the-isg-correctly-on-the-client) and sets its startup mode to Automatic. It's a protected service so can't be disabled or modified using Services snap-in.
-
-* ISG Authorization requires active Internet connection to communicate with the global ISG network.
-
-* Recommended to perform a reboot regardless of whether you are deploying signed or unsigned version of the "SignedAndReputable" App Control base policy.
-
-
-
-After finishing deploying the SignedAndReputable base policy, if there is an app that is getting blocked and you want to allow it, you can create Supplemental policies to expand your base policy. To do that, you have multiple options.
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for Apps Already Installed
-
-The following commands use the `-Deploy` optional switch parameter, meaning after Supplemental policy creation, they are automatically deployed on the system.
-
-If you chose the Signed path, omit it from the commands and instead use the [Deploy-SignedWDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig) cmdlet to Sign and Deploy the Supplemental policy xml files.
-
-### Based on Signer Rules, Hashes, File Names Etc.
-
-```powershell
-New-SupplementalWDACConfig -Normal -ScanLocation "C:\Program Files\Program" -SuppPolicyName "App's Name" -PolicyPath "C:\SignedAndReputable.xml" -Deploy
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--normal)
-
-
-
-### Based on File Path With One or More Wildcard Characters
-
-```powershell
-New-SupplementalWDACConfig -FilePathWildCards -WildCardPath "C:\Program Files\Program\*" -SuppPolicyName "App's Name" -PolicyPath
-"C:\SignedAndReputable.xml" -Deploy
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--filepathwildcards)
-
-
-
-### Based on an Installed Windows App’s Name
-
-```powershell
-New-SupplementalWDACConfig -InstalledAppXPackages -PackageName "*App's name*" -SuppPolicyName "App's name" -PolicyPath "C:\SignedAndReputable.xml" -Deploy
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-SupplementalWDACConfig#new-supplementalwdacconfig--installedappxpackages)
-
-
-
- -
-
-
-
-
-## Creating Supplemental Policy for New App Installations or Apps Already Installed
-
-If the app you are trying to allow isn't installed, and when you try to install it you see a blocked/error message, you can use the following syntaxes to allow them to run and then automatically create Supplemental policy for them.
-
-These methods also work for apps that were installed prior to deploying the "SignedAndReputable" base policy and now you want to allow them to run by creating Supplemental policy for them.
-
-You can create a Supplemental policy for more than 1 app at a time by browsing for multiple apps' install directories using the commands below.
-
-
-
-### Based on App’s Install Directory and Other Signals - Unsigned Version
-
-```powershell
-Edit-WDACConfig -AllowNewApps -SuppPolicyName "App's Name" -PolicyPath "C:\SignedAndReputable.xml"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Edit-WDACConfig#edit-wdacconfig--allownewapps)
-
-
-
-### Based on App’s Install Directory and Other Signals - Signed Version
-
-```powershell
-Edit-SignedWDACConfig -AllowNewApps -CertPath "C:\Certificate.cer" -SuppPolicyName "App's Name" -PolicyPath "C:\SignedAndReputable.xml" -CertCN "App Control Certificate"
-```
-
-* [Parameter info](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Edit-SignedWDACConfig#edit-signedwdacconfig--allownewapps)
-
-
-
- -
-
-
-
-
-## Security Considerations
-
-One of the differences between using **ISG in an App Control policy** vs using **Smart App Control** (which also use ISG) is that App Control policy + ISG rule option passes along reputation from app installers to the binaries they write to disk, it can over-authorize files in some cases. For example, if the installer launches the app upon completion, any files the app writes during that first run will also be allowed.
-
-Smart App Control however doesn't do this, it will trust the installer file itself if it's trustworthy and subsequently checks the trustworthiness of any binaries the installer tries to use and write to the disk, if any of those binaries or components can't be verified or are malicious, they get blocked.
-
-Explained more in here:
-
-* [Security considerations with the ISG option](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/use-appcontrol-with-intelligent-security-graph#security-considerations-with-the-isg-option)
-
-* [Smart app control has blocked part of this app](https://support.microsoft.com/en-us/topic/smart-app-control-has-blocked-part-of-this-app-0729fff1-48bf-4b25-aa97-632fe55ccca2)
-
-
-
- -
-
-
-
-
-## What to Do When There Is an Update for an Allowed App?
-
-If you've created a Supplemental policy for an app that is already installed and now there is a newer version of that app available, you have multiple options:
-
-1. If the Supplemental policy that you created to allow that app is based on FilePath with wildcards, then the app can be updated and no change in policy is required.
-
-2. If the Supplemental policy is based on [PFN (Package Family Name)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/manage-packaged-apps-with-appcontrol) of the app, available only for apps that use [MSIX](https://learn.microsoft.com/en-us/windows/msix/overview) installers, like some of the modern apps installed through Microsoft Store, then you don't need to take any action and the app will be updated without any issues.
-
-3. If the Supplemental policy is only based on the app's digital signature, which is common for well-made apps, then you don't need to take any further action. As long as the new version of the app has the same digital signature / developer identity, then it will be allowed to run.
-
-4. If the Supplemental policy is based on individual File Paths (in contrast to wildcard FilePath rules), or based on [FileName rules](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/select-types-of-rules-to-create#table-3--specificfilenamelevel-options), then most likely there is no need for any further action to be taken as long as the new app's version uses the same file names or the same file paths for its components.
-
-5. If the Supplemental policy is based on Hash of the app's files, either partially (mixed with signer rules) or entirely (for apps without any digital identity/signature) then all you have to do is to remove the deployed Supplemental policy and create a new Supplemental policy for the app using live audit mode in the module as explained above. Don't need to reboot immediately, but to finish the removal process of a Supplemental policy, whether it's signed or unsigned, a reboot will be eventually needed.
-
-
 +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ -
-
-
- +* Keep the xml file(s) of the deployed base policy(s) in a safe place, they are needed, along with the certificate that signed them, if you decide to disable or modify the signed deployed App Control policy later on.
+* Keep the xml file(s) of the deployed base policy(s) in a safe place, they are needed, along with the certificate that signed them, if you decide to disable or modify the signed deployed App Control policy later on.
 -
-
-
- -
-
-
- +
+ +
+
+
+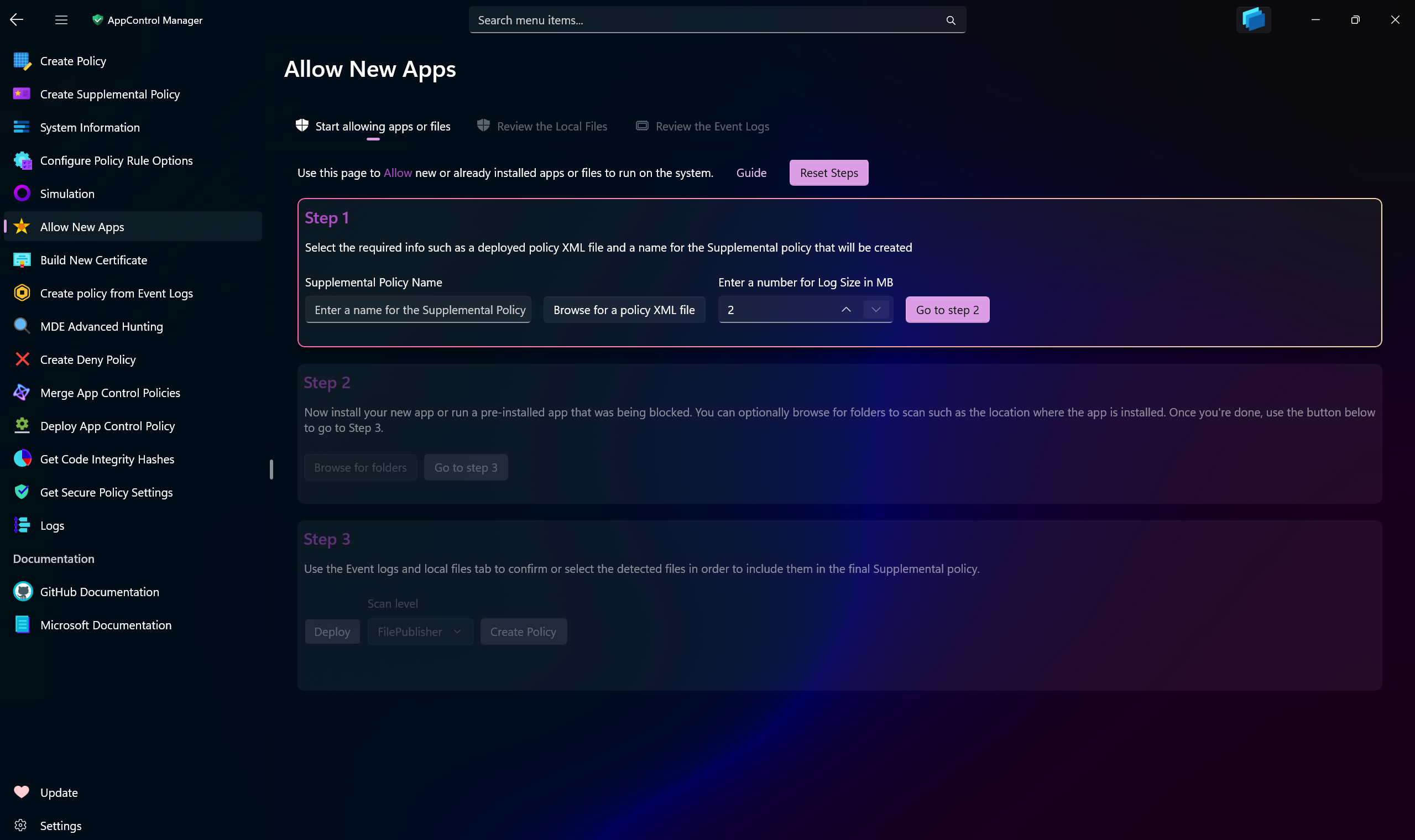 +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+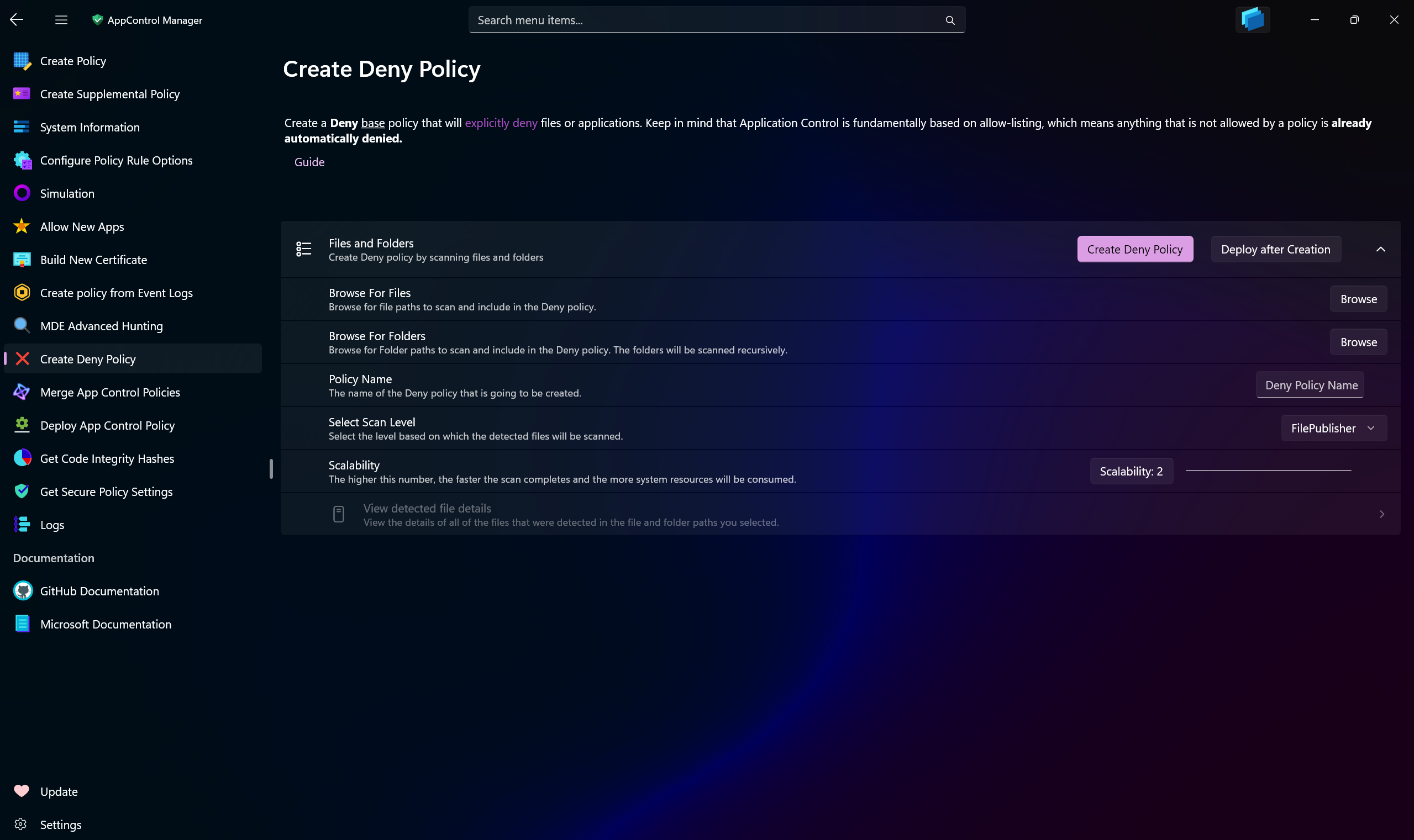 +
+
+
+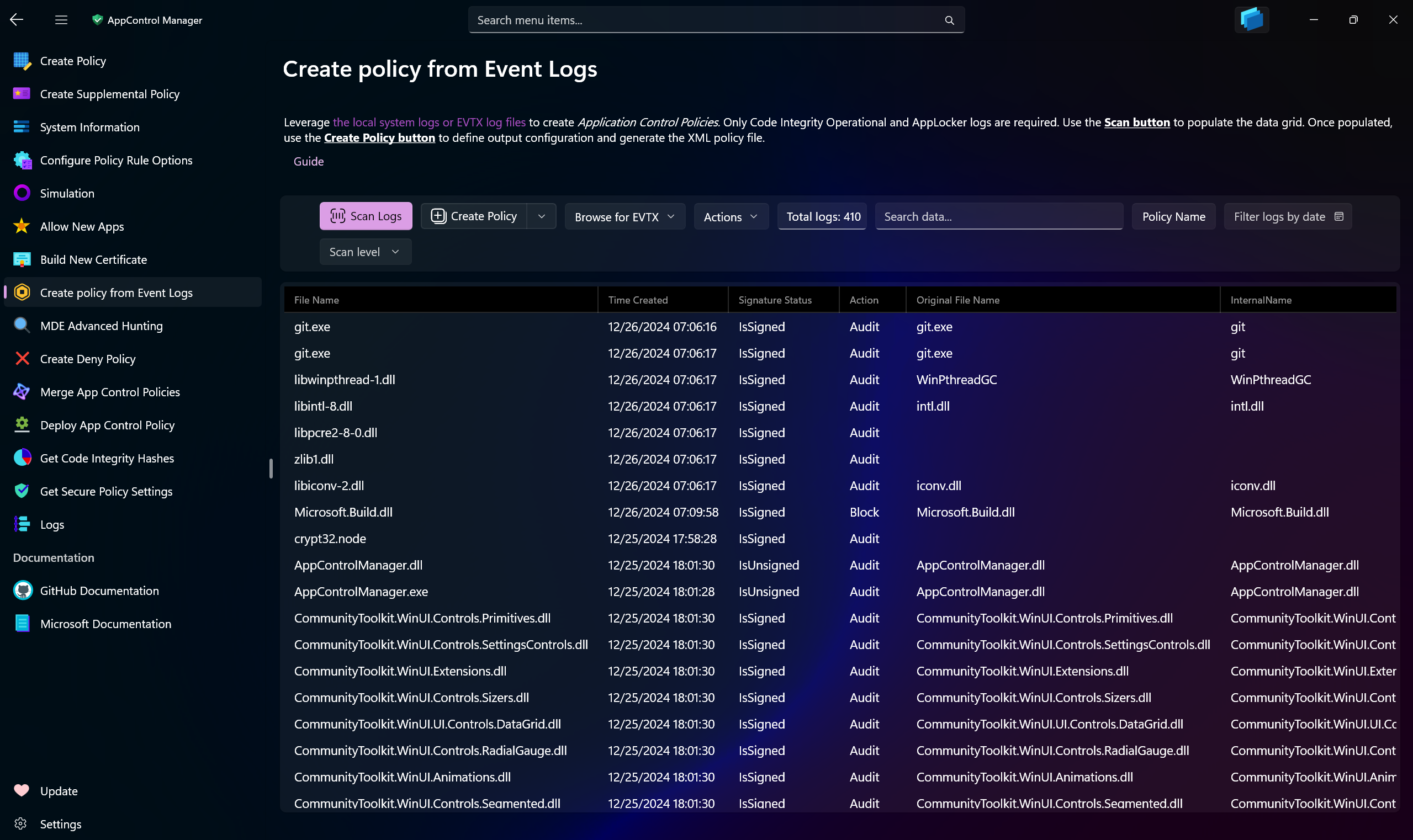 +
+
+
+ +
+
+
+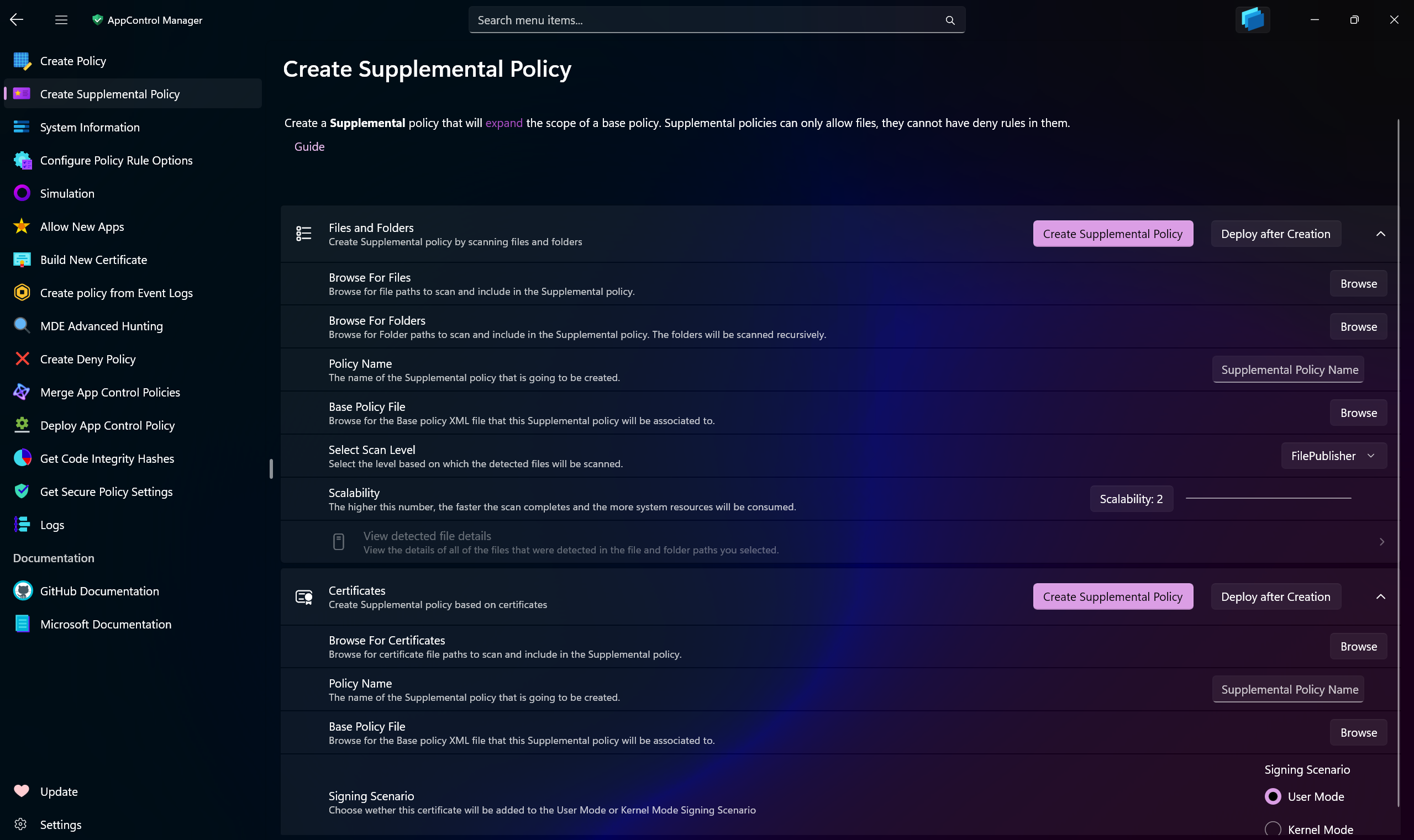 +
+
+
+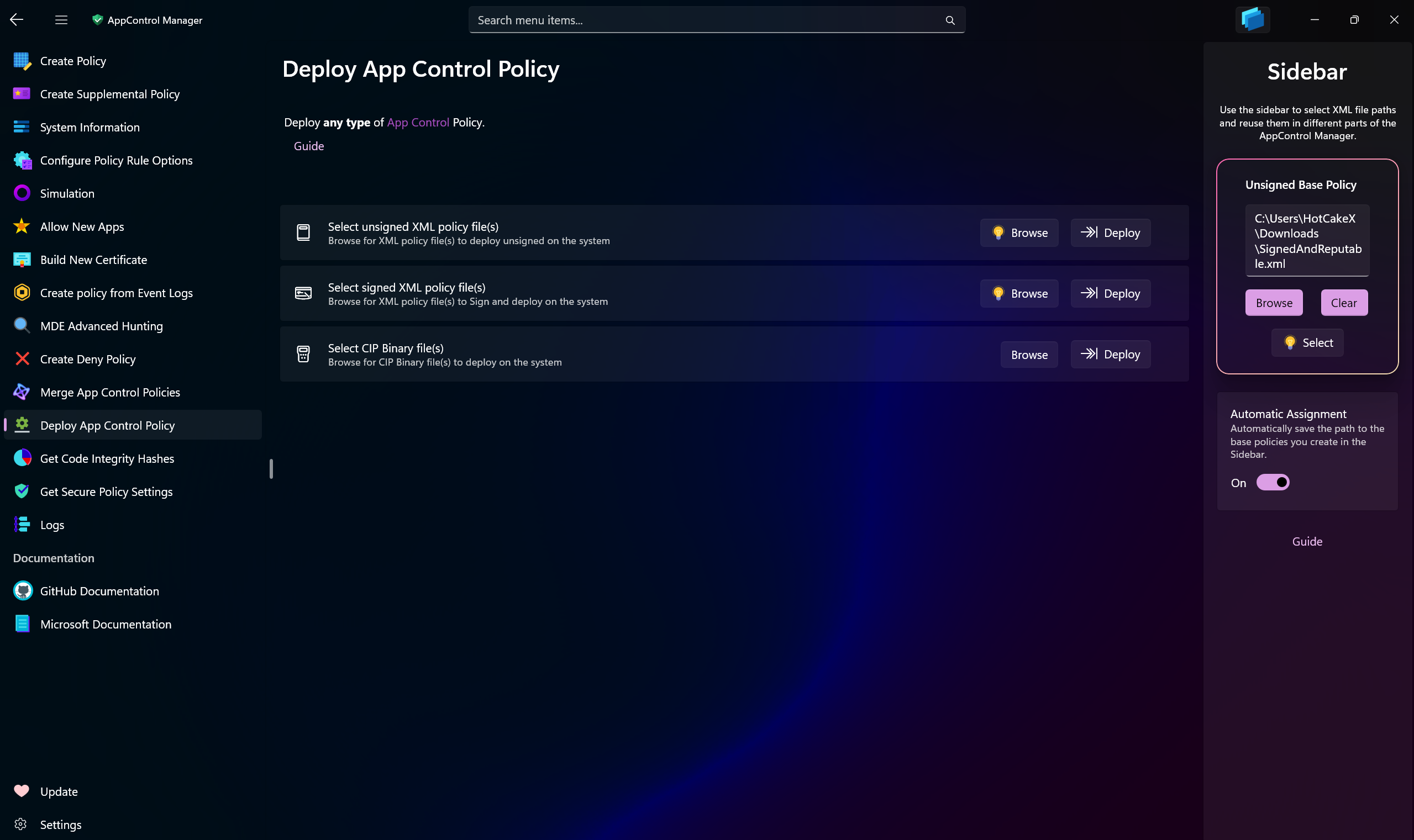 +
+
+
+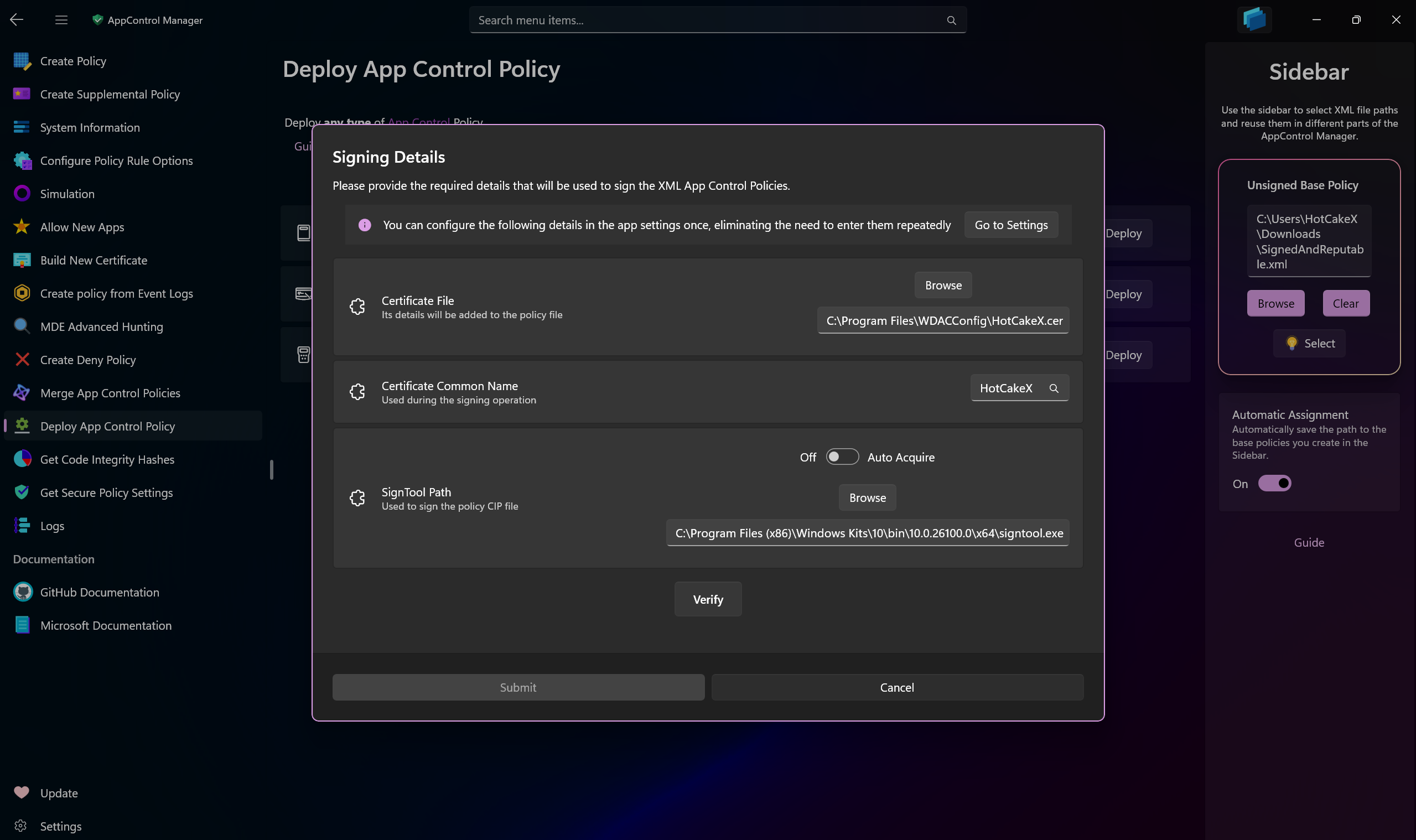 +
+
+
+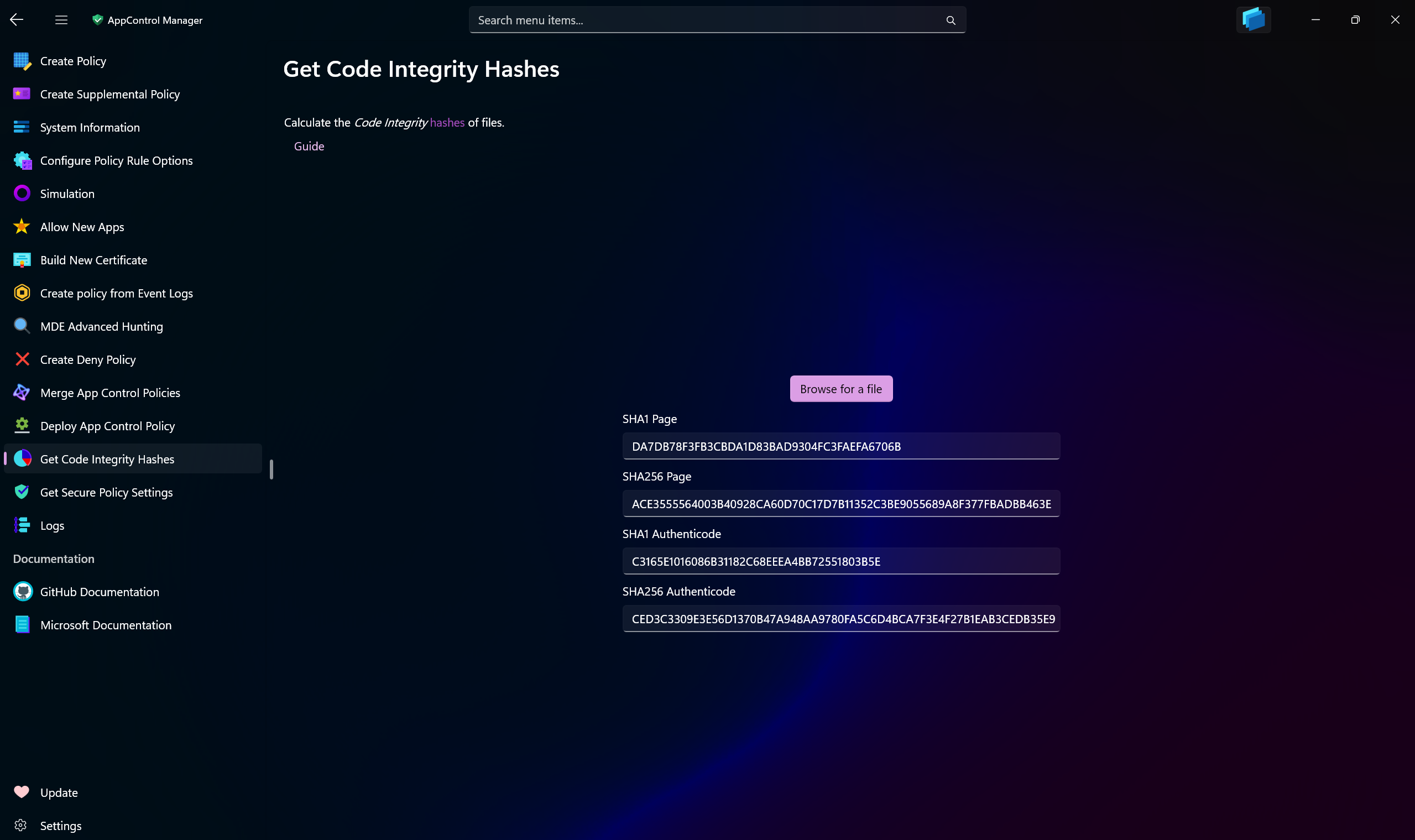 +
+
+
+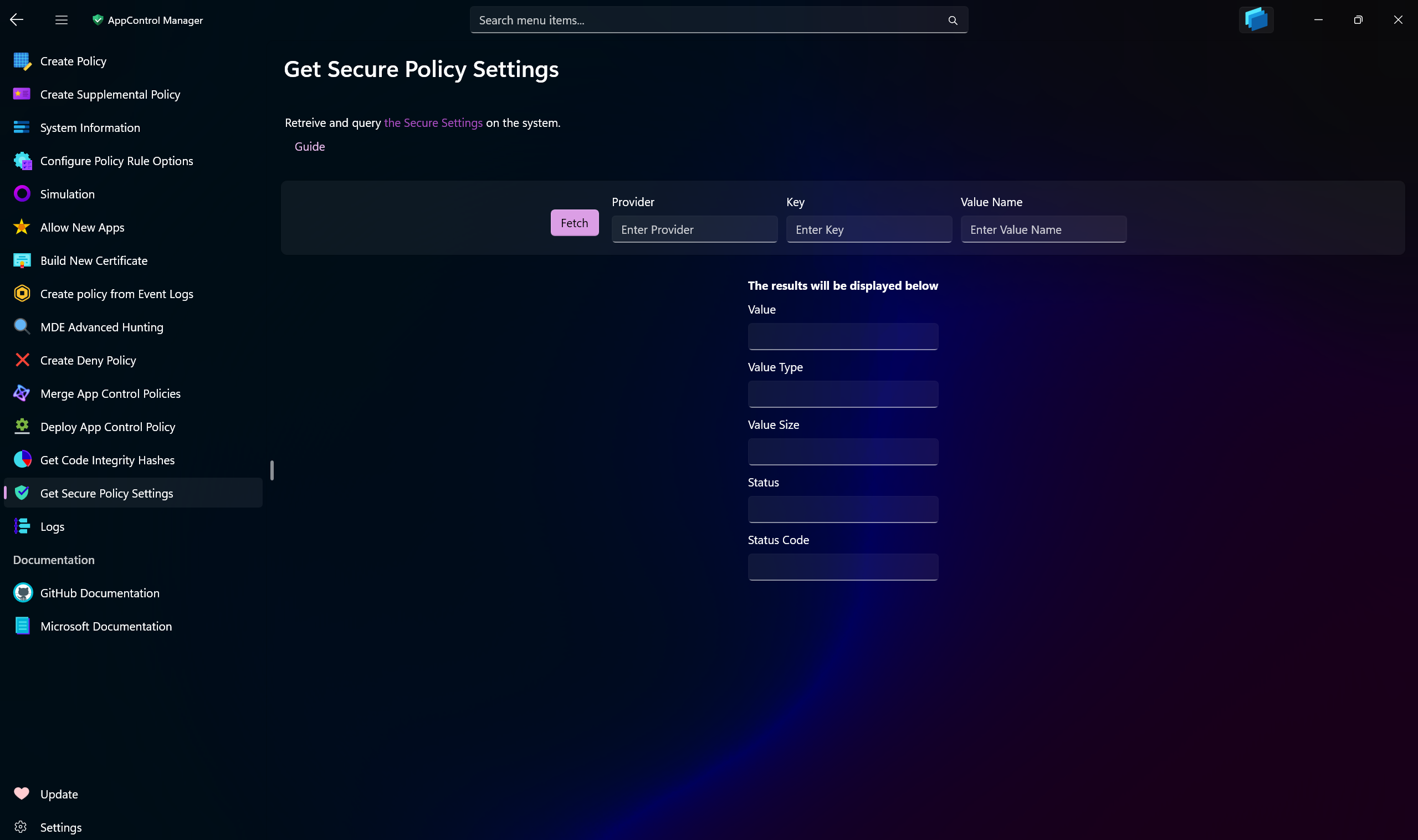 +
+
+
+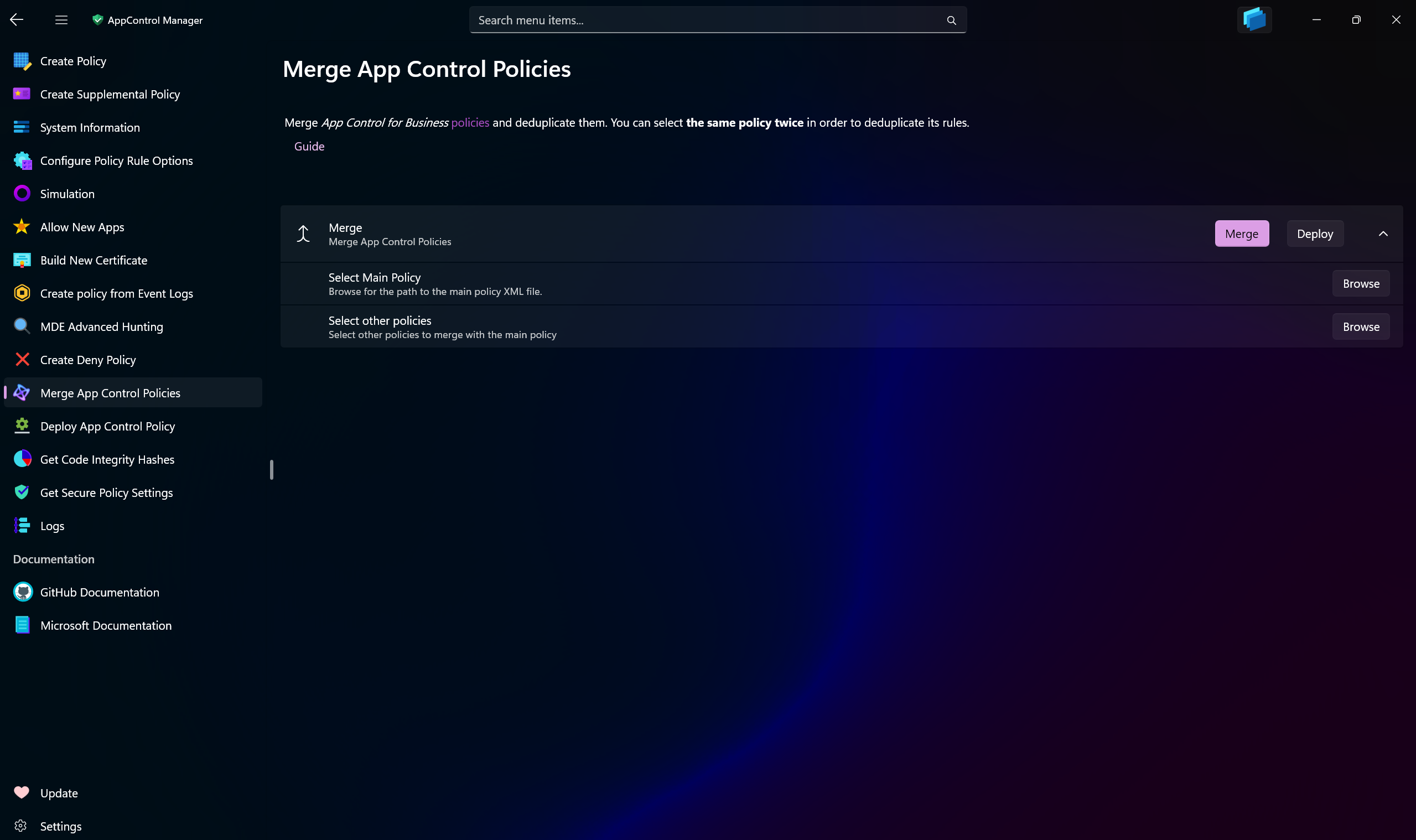 +
+
+
+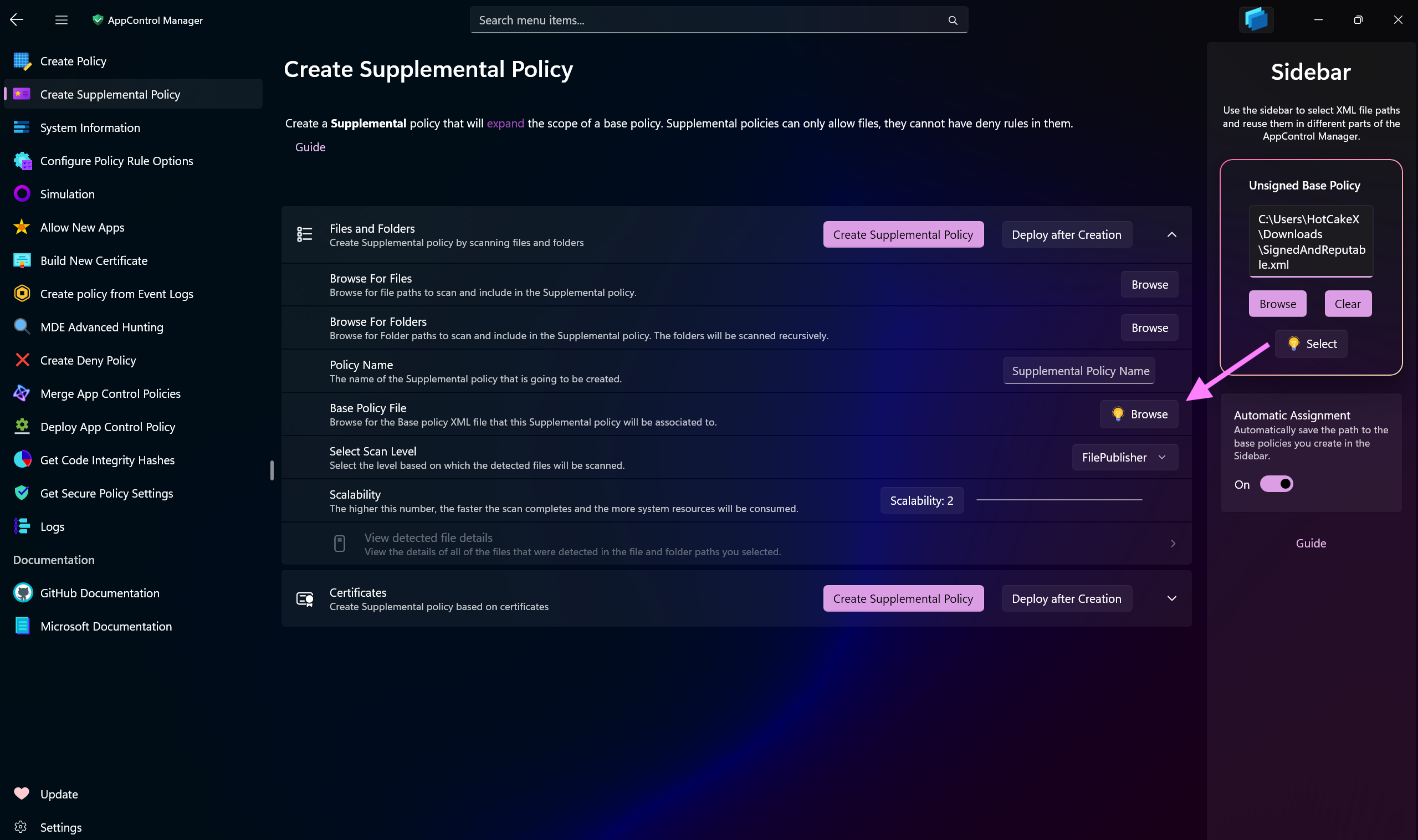 +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ +
+
+
+ [App Control for Business](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction)
-
[App Control for Business](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction)
-  -
-
-
- -
-
-
- -
-
-
- -
-
-
-%20Policies%20Using%20The%20WDACConfig%20Module%20-%20low%20res.png) -
-## Syntax
-
-```powershell
-Invoke-WDACSimulation
- [-XmlFilePath]
-
-## Syntax
-
-```powershell
-Invoke-WDACSimulation
- [-XmlFilePath]  -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- +
+ 
 -```powershell
-Install-Module -Name 'WDACConfig' -Scope 'AllUsers' -Force
-```
+
-```powershell
-Install-Module -Name 'WDACConfig' -Scope 'AllUsers' -Force
-```
+ | [Microsoft Defender For Endpoint Advanced Hunting With WDACConfig Module](https://youtu.be/oyz0jFzOOGA?si=tJbFbzRJNy79lUo7) |
-|
| [Microsoft Defender For Endpoint Advanced Hunting With WDACConfig Module](https://youtu.be/oyz0jFzOOGA?si=tJbFbzRJNy79lUo7) |
-|  | [Sandboxing-like capabilities in the App Control Policies](https://www.youtube.com/watch?v=cp7TaTNPZE0) |
-|
| [Sandboxing-like capabilities in the App Control Policies](https://www.youtube.com/watch?v=cp7TaTNPZE0) |
-|  | [Create, Deploy & Audit App Control Policies](https://www.youtube.com/watch?v=JSwrfe9zYY4) |
-|
| [Create, Deploy & Audit App Control Policies](https://www.youtube.com/watch?v=JSwrfe9zYY4) |
-|  | [How To Set And Query Secure Settings in App Control Policies](https://www.youtube.com/watch?v=hNpzYlOMCys) |
-|
| [How To Set And Query Secure Settings in App Control Policies](https://www.youtube.com/watch?v=hNpzYlOMCys) |
-|  | [How To Create And Deploy Signed App Control Policies](https://www.youtube.com/watch?v=nZ5c9ceaEwA) |
-|
| [How To Create And Deploy Signed App Control Policies](https://www.youtube.com/watch?v=nZ5c9ceaEwA) |
-| %20Policies%20Using%20The%20WDACConfig%20Module%20-%20low%20res.png) | [Simulating App Control Deployment in Windows](https://www.youtube.com/watch?v=A0bKDaeYomg) |
-|
| [Simulating App Control Deployment in Windows](https://www.youtube.com/watch?v=A0bKDaeYomg) |
-|  | [Create Code Signing Certificate Using Windows Server](https://youtu.be/RSYJ64BlS9Y?si=t6TlcYzsMwteG1M9) |
-
-
| [Create Code Signing Certificate Using Windows Server](https://youtu.be/RSYJ64BlS9Y?si=t6TlcYzsMwteG1M9) |
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
- -
-
-
-